
The first thing you do when you hear that email notification is check the sender, right? It is the quickest way to figure out who the email is from, as well as the likely content.
But did you know each email comes with a lot more information than what appears in most email clients? There’s a host of information about the sender included in the email header—information you can use to trace the email back to the source.
Here’s how to trace that email back to where it came from, and why you might want to.
Why Trace an Email Address?
Before learning how to trace an email address, let’s consider why you would do it in the first place.
In this day and age, malicious emails are all too frequent. Scams, spam, malware, and phishing emails are a common inbox sight. If you trace an email back to its source, you have a slight chance of discovering who (or where!) the email comes from.
In other cases, you can trace the origin of an email to block a persistent source of spam or abusive content, permanently removing it from your inbox; server administrators trace emails for the same reason.
(If you want to prevent your own email identity from being revealed, learn to send completely anonymous emails.)
How to Trace an Email Address
You can trace an email address to its sender by looking at the full email header. The email header contains routing information and email metadata—information you don’t normally care about. But that information is vital to tracing the source of the email.
Most email clients don’t display the full email header as standard because it is full of technical data and somewhat useless to an untrained eye. However, most email clients do offer a way of checking out the full email header. You just need to know where to look, as well as what you’re looking at.
- Gmail Full Email Header: Open your Gmail account, then open the email you want to trace. Select the drop-down menu in the top-right corner, then Show original from the menu.
- Outlook Full Email Header: Double-click the email you want to trace, the head to File > Properties. The information appears in the internet headers
- Apple Mail Full Email Header: Open the email you wish to trace, then head to View > Message > Raw Source.
Of course, there are countless email clients. A quick internet search will reveal how to find your full email header in your client of choice. Once you have the full email header open, you’ll understand what I meant by “full of technical data.”
Understanding the Data in a Full Email Header
It looks like a lot of information. However, consider the following: you read the email header chronologically, from bottom to top (i.e., oldest information at the bottom), and that each new server the email travels through adds Received to the header.
Check out this sample email header taken from my MakeUseOf Gmail account:
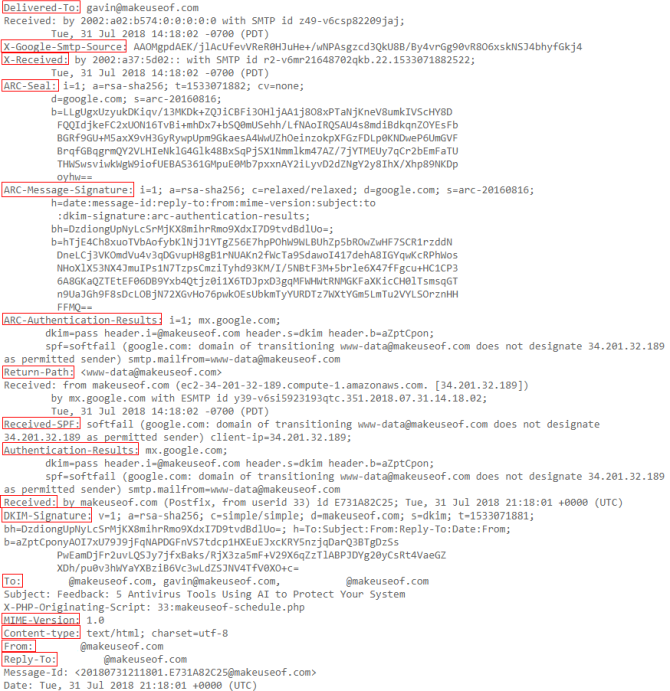
Gmail Email Header Lines
There’s a lot of information. Let’s break it down. First, understand what each line means (reading from bottom to top).
- Reply-To: The email address you send your response too.
- From: Displays the message sender; it is easy to forge.
- Content-type: Tells your browser or email client how to interpret the content of the email. The most common character sets are UTF-8 (seen in the example) and ISO-8859-1.
- MIME-Version: Declares the email format standard in use. The MIME-Version is typically “1.0.”
- Subject: The subject of the email contents.
- To: The intended recipients of the email; may show other addresses.
- DKIM-Signature: DomainKeys Identified Mail authenticates the domain the email was sent from and should protect against email spoofing and sender fraud.
- Received: The “Received” line lists each server that the email travels through before hitting your inbox. You read “Received” lines from bottom to top; the bottom-most line is the originator.
- Authentication-Results: Contains a record of the authentication checks carried out; can contain more than one authentication method.
- Received-SPF: The Sender Policy Framework (SPF) forms part of the email authentication process that stops sender address forgery.
- Return-Path: The location where non-send or bounce messages end up.
- ARC-Authentication-Results: The Authenticated Receive Chain is another authentication standard; ARC verifies the identities of the email intermediaries and servers that forward your message to its final destination.
- ARC-Message-Signature: The signature takes a snapshot of the message header information for validation; similar to DKIM.
- ARC-Seal: “Seals” the ARC authentication results and the message signature, verifying their contents; similar to DKIM.
- X-Received: Differs to “Received” in that it is considered non-standard; that is to say, it might not be a permanent address, such as a mail transfer agent or Gmail SMTP server. (See below.)
- X-Google-Smtp-Source: Shows the email transferring using a Gmail SMTP server.
- Delivered-To: The final recipient of the email in this header.
You don’t have to understand what all of these things mean to trace an email. But if you learn to look through the email header, you can quickly begin to trace the email sender.
Tracing the Original Sender of an Email
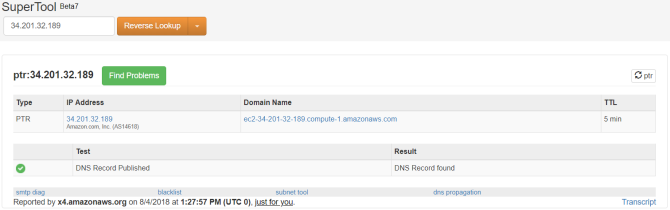
To trace the IP address of the original email sender, head to the first Received in the full email header. Alongside the first Received line is the IP address of the server that sent the email. Sometimes, this appears as X-Originating-IP or Original-IP.
Find the IP address, then head to MX Toolbox. Enter the IP address in the box, change the search type to Reverse Lookup using the drop-down menu, then hit Enter. The search results will display a variety of information relating to the sending server.
Unless the originating IP address is one of the millions of private IP addresses. In that case, you will meet the following message:
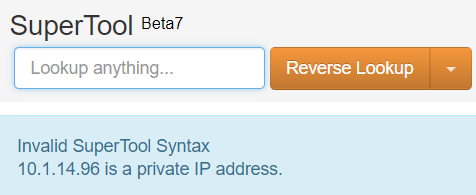
The following IP ranges are private:
- 0.0.0-10.255.255.255
- 16.00-172.31.255.255
- 168.0.0-192.168.255.255
- 0.0.0-239.255.255.255
IP address lookups for those ranges will not return any results.
3 Free Tools to Trace Emails and IP Addresses
Of course, there are some handy tools out there that automate this process for you. It is handy to learn about full email headers and their contents, but sometimes you need quick information.
Check out the following header analyzers:
- GSuite Toolbox Messageheader
- MX Toolbox Email Header Analyzer
- IP-Address Email Header Trace(email header analyzer + IP address tracer)
The results don’t always match up though.
The results don’t always match up though. In the below example, I know that the sender is nowhere near the alleged location stated as Ashburn, Virginia:
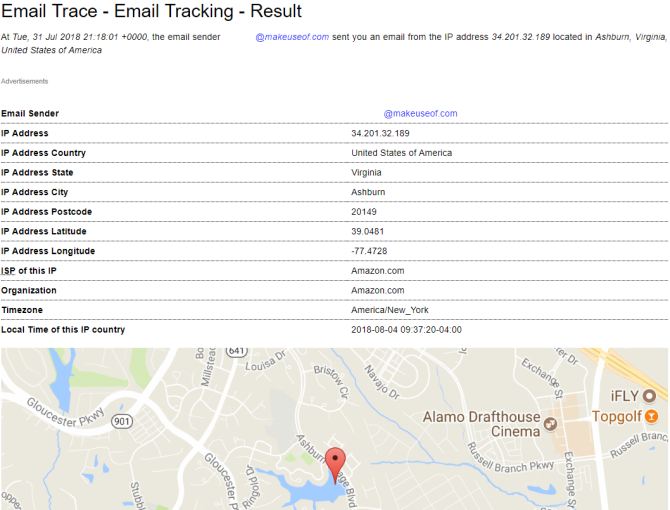
In that, your success with tracing an email will vary depending on the email provider of the sender. If you’re trying to trace an email sent from a Gmail account, you’ll only find out the location of the last Google server that processed your email—not the IP address of the original sender.
Can You Really Trace an IP Address from an Email?
There are instances where tracing an IP address through the email header is useful. A particularly irritating spammer perhaps, or the source of regular phishing emails. Certain emails will only come from certain locations; your PayPal emails won’t originate in China, for instance.
However, as it is trivially easy to spoof email headers, take all the results you find with a pinch of salt. Finally, are you interested in learning more about email spoofing? Take a look at our guide to email security protocols for a great starting point.
Read the full article: How to Trace Emails Back to Their Source IP Address
Read Full Article
No comments:
Post a Comment