A blog about how-to, internet, social-networks, windows, linux, blogging, tips and tricks.
29 September 2018
Two weeks with a $16,000 Hasselblad kit
For hobbyist photographers like myself, Hasselblad has always been the untouchable luxury brand reserved for high-end professionals.
To fill the gap between casual and intended photography, they released the X1D — a compact, mirrorless medium format. Last summer when Stefan Etienne reviewed the newly released camera, I asked to take a picture.
After importing the raw file into Lightroom and flipping through a dozen presets, I joked that I would eat Ramen packets for the next year so I could buy this camera. It was that impressive.

XCD 3.5/30mm lens
Last month Hasselblad sent us the XCD 4/21mm (their latest ultra wide-angle lens) for a two-week review, along with the X1D body and XCD 3,2/90mm portrait lens for comparison. I wanted to see what I could do with the kit and had planned the following:
- Swipe right on everyone with an unflattering Tinder profile picture and offer to retake it for them
- Travel somewhere with spectacular landscapes
My schedule didn’t offer much time for either, so a weekend trip to the cabin would have to suffice.
[gallery type="slideshow" link="none" columns="1" size="full" ids="1722181,1722182,1722183,1722184,1722185,1722186,1722187,1722188,1722201"]As an everyday camera
The weekend upstate was rather quiet and uneventful, but it served to be the perfect setting to test out the camera kit because the X1D is slow A. F.
It takes approximately 8 seconds to turn on, with an additional 2-3 seconds of processing time after each shutter click — top that off with a slow autofocus, slow shutter release and short battery life (I went through a battery within a day, approximately 90 shots fired). Rather than reiterating Stefan’s review, I would recommend reading it here for full specifications.
Coming from a Canon 5D Mark IV, I’m used to immediacy and a decent hit rate. The first day with the Hasselblad was filled with constant frustration from missed moments, missed opportunities. It felt impractical as an everyday camera until I shifted toward a more deliberate approach — reverting back to high school SLR days when a roll of film held a limited 24 exposures.
When I took pause, I began to appreciate the camera’s details: a quiet shutter, a compact but sturdy body and an intuitive interface, including a touchscreen LCD display/viewfinder.
[gallery type="slideshow" link="none" columns="1" size="full" ids="1722796,1722784,1722775"]Nothing looks or feels cheap about the Swiss-designed, aluminum construction of both the body and lenses. It’s heavy for a mirrorless camera, but it feels damn good to hold.
XCD 4/21mm lens
[gallery type="slideshow" link="none" columns="1" size="full" ids="1722190,1722191,1722489,1722490"]Dramatic landscapes and cityscapes without an overly exaggerated perspective — this is where the XCD 4/21mm outperforms other super wide-angle lenses.
With a 105° angle of view and 17mm field of view equivalent on a full-framed DSLR, I was expecting a lot more distortion and vignetting, but the image automatically corrected itself and flattened out when imported into Lightroom. The latest deployment of Creative Cloud has the Hasselblad (camera and lens) profile integrated into Lightroom, so there’s no need for downloading and importing profiles.
Oily NYC real estate brokers should really consider using this lens to shoot their dinky 250 sq. ft. studio apartments to feel grand without looking comically fish-eyed.
XCD 3,2/90mm lens
The gallery below was shot using only the mirror’s vanity lights as practicals. It was also shot underexposed to see how much detail I could pull in post. Here are the downsized, unedited versions, so you don’t have to wait for each 110mb file to load.
[gallery type="slideshow" link="none" columns="1" size="full" ids="1722193,1722194,1722195,1722196"]I’d like to think that if I had time and was feeling philanthropic, I could fix a lot of love lives on Tinder with this lens.
Where it shines
Normally, images posted in reviews are unedited, but I believe the true test of raw images lies in post-production. This is where the X1D’s slow processing time and quick battery drainage pays off. With the camera’s giant 50 MP 44 x 33mm CMOS sensor, each raw file was approximately 110mb (compared to my Mark IV’s 20-30mb) — that’s a substantial amount of information packed into 8272 x 6200 pixels.
Resized to 2000 x 1500 pixels and cropped to 2000 x 1500 pixels:

While other camera manufacturers tend to favor certain colors and skin tones, Dan Wang, a Hasselblad rep, told me, “We believe in seeing a very natural or even palette with very little influence. We’re not here to gatekeep what color should be. We’re here to give you as much data as possible, providing as much raw detail, raw color information that allows you to interpret it to your extent.”
As someone who enjoys countless hours tweaking colors, shifting pixels and making things pretty, I’m appreciative of this. It allows for less fixing, more creative freedom.

Who is this camera for?
My friend Peter, a fashion photographer (he’s done editorial features for Harper’s Bazaar, Cosmopolitan and the likes), is the only person I know who shoots on Hasselblad, so it felt appropriate to ask his opinion. “It’s for pretentious rich assholes with money to burn,” he snarked. I disagree. The X1D is a solid step for Hasselblad to get off heavy-duty tripods and out of the studio.
At this price point though, one might expect the camera to do everything, but it’s aimed at a narrow demographic: a photographer who is willing to overlook speediness for quality and compactibility.
With smartphone companies like Apple and Samsung stepping up their camera game over the past few years, the photography world feels inundated with inconsequential, throw-away images (self-indulgent selfies, “look what I had for lunch,” OOTD…).
My two weeks with the Hasselblad was a kind reminder of photography as a methodical art form, rather than a spray and pray hobby.
Reviewed kit runs $15,940, pre-taxed:
- X1D Medium Format body: $8,995.00 (currently on sale at BH for $6,495.00)
- XCD 4/21mm lens: $3,750.00
- XCD 3,2/90mm lens:” $3,195.00
Read Full Article
How to Password Protect a Folder in Windows

Take a second to consider how much sensitive information you have stored on your computer at this moment. Bank information? Family photos? Financial documents?
As secure as your files feel on your PC, they’re also prime targets for malicious intent. Password protecting your sensitive folders is a basic security step. Think of it as a virtual vault, which encrypts whatever files or additional folders you’d need kept safe.
Read on to learn how to create a password-protected folder to keep your precious files protected, and sneaky onlookers at bay.
Method 1: Text-Based Folder Lock
While Windows 10 doesn’t allow users to password protect folders by default, you can use a batch script to lock folders using a password of your choice. If you aren’t familiar with batch scripts, here’s a primer.
Start by navigating to the folder you’d like to lock. I’ll create a new folder to use as a virtual safe named Safe.
Double-click the folder. You’ll be creating your batch file within the directory that’ll store your locked folder. Create an empty text document within your folder by right-clicking an empty space and selecting New > Text Document.
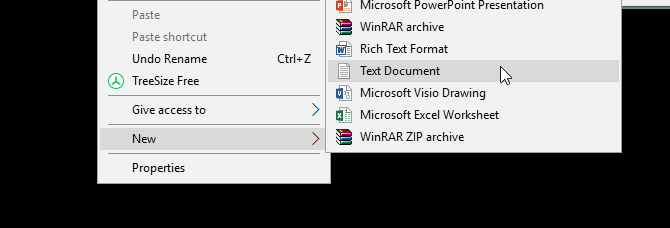
Within this document, copy and paste the following code:
cls
@ECHO OFF
title Folder Locker
if EXIST "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" goto UNLOCK
if NOT EXIST Locker goto MDLOCKER
:CONFIRM
echo Are you sure u want to Lock the folder(Y/N)
set/p "cho=>"
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren Locker "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
attrib +h +s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
echo Folder locked
goto End
:UNLOCK
echo Enter password to Unlock folder
set/p "pass=>"
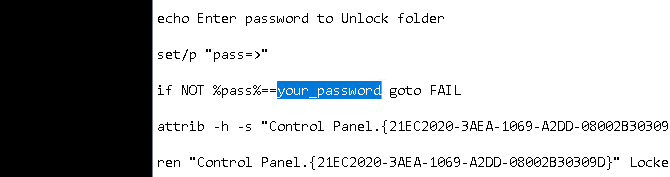
if NOT %pass%==your_password goto FAIL
attrib -h -s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
ren "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" Locker
echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDLOCKER
md Locker
echo Locker created successfully
goto End
:End
To set your password, change the your_password bit in the line if NOT “%pass%==your_password” goto FAIL to a password of your choice:
Once you’ve added your password, head to File > Save As within your Notepad program. Name it anything you’d like, Locker in my case, but ensure you add a .bat extension to your file. In my case, I will name my file Locker.bat (ensuring I’ve included the extension).
Double-click the BAT file to create your Locker folder. This is the folder that will be locked with your password. You should now have a folder and a file named Locker.
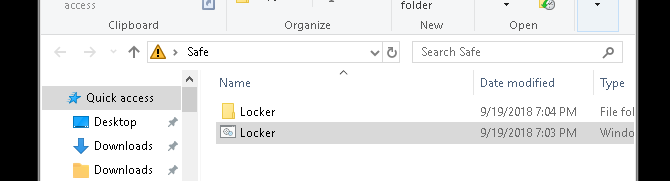
Place all your sensitive documents within this Locker folder. Once you’ve placed your files, double-click your Locker.bat file again. A command prompt will open asking if you want to lock your folder. Input Y and press Enter.
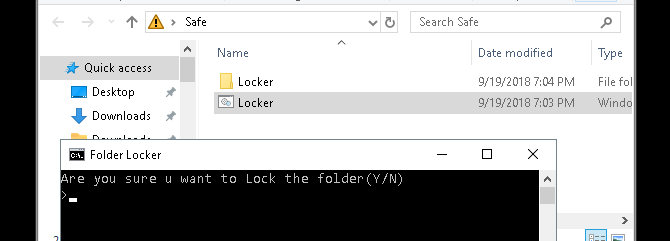
Poof! Your folder should disappear. This is a natural byproduct of your BAT file.
To access your files again, double-click on your Locker.bat file. You will be prompted to enter the password you added when creating the file.
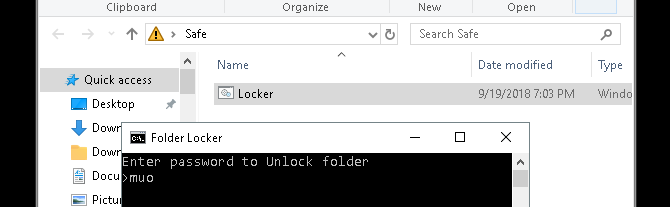
Voila! If you enter your password correctly, your Locker folder will reappear again.
Note: This BAT file can be changed via your PC. That means others who are familiar with this trick may be able to change your password. For the most part, however, this nifty little trick will add a much needed buffer to your most sensitive local documents!
If you’d like to learn more about what BAT files can do, we’ve got you covered.
Method 2: ZIP Folder Lock
While the above trick uses the default Notepad program, you can also both lock and condense your sensitive documents using a popular desktop program named 7-Zip.
Typically used to unzip folders and extract files, 7-Zip also allows users to password protect their folders. To follow this method, first download 7-Zip.
Once 7-Zip is downloaded and installed, click the start menu and type 7zip. Select the 7-Zip File Manager option. Then, locate the file or folder you want to protect, click on it, and click the Add option at the top of the window.
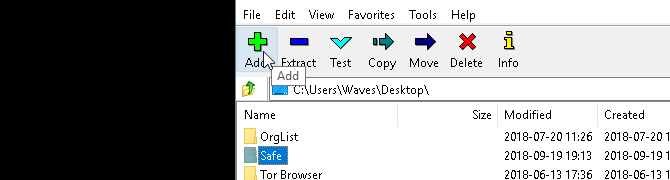
Next, enter your new password in the Encryption section. When you’re done, click OK. Check your folder location and you’ll find a ZIP file named the same as your original folder.
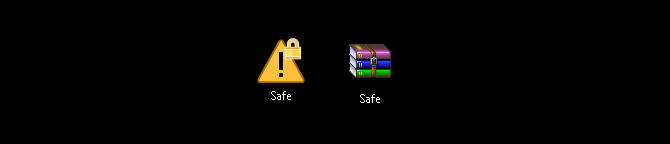
Now that you have your zipped file, delete your original folder (as keeping it would defeat the purpose of password protecting your new ZIP file).
It’s a good idea to create another containing folder for your zipped file, as unzipping it may scatter your files in a directory. In the example below, the Sensitive Documents folder will hold my zipped Safe file.
Right-click your zip file and select 7-Zip > Extract Here. You’ll be prompted to enter your password.
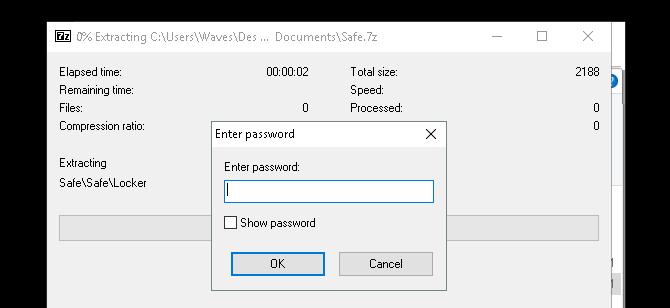
Enter your password and your files will appear in your directory.
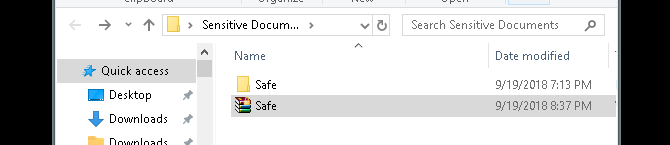
That’s it! While this method isn’t exactly timely, since you have to undergo the whole process every time you need to add or view your files, it works perfectly and only uses this trusted software.
Method 3: Hide Files and Folders
Now that you’ve locked your folder, you can also take the additional step of hiding your folder from view.
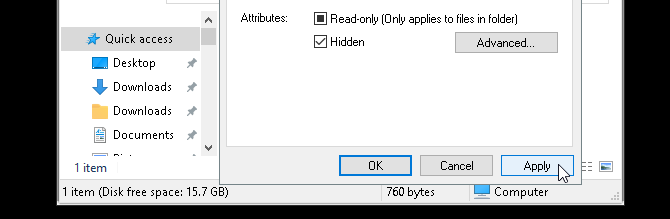
Right-click a file or folder or your choice and select Properties. Check the Hidden option beside Attributes. Click Apply and then OK.
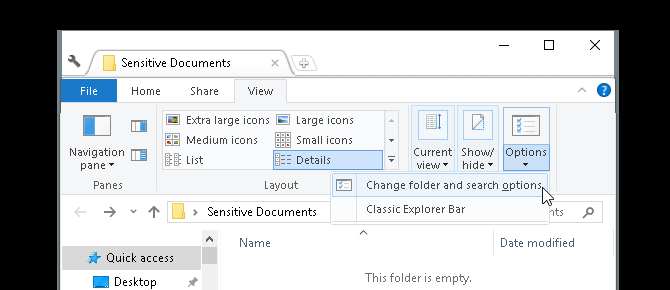
Your file or folder should now disappear. To view your folder again, click on the View tab of your Windows 10 file manager. Then, select Options > Change folder and search options.
In the following File Options window, click on the View tab. Finally, click on the option labeled Show hidden files, folders, and drives under Hidden files and folders. Click Apply and then OK.
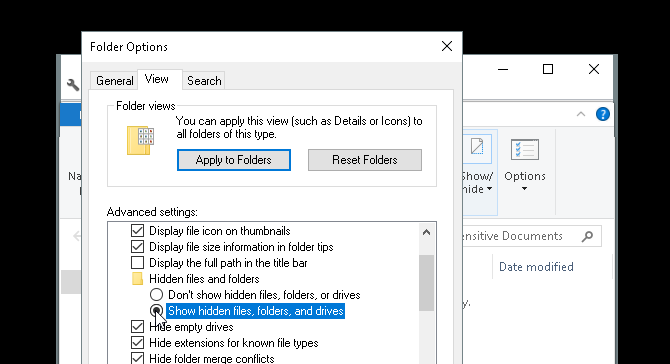
You should now be able to view your file or folder. To revert your file or folder back to hidden, head to your File Options window again and select Don’t show hidden files, folders, or drives. That’s it!
Lock Your Windows Folders to Keep Your Data Safe
With the simple methods above, you can choose to implement either one or all three. No matter which you pick, you can rest assured that your previous sensitive documents are safe under an additional layer of protection not enabled by default on your PC.
Sometimes, all it takes is a password lock to prevent theft. That applies to the virtual world as much it does to the real world. And it’s up to you to bulletproof your PC with the best security tools for your computer.
Read the full article: How to Password Protect a Folder in Windows
Read Full Article
7 Ways to Download Videos From Instagram

Ah, Instagram video. A yardstick by which we can all measure our online popularity—or not.
We’ve already shown you everything you need to know about Instagram video, but what if you want to download them, share them, and view them at your leisure?
Whether it’s your own amazing creations or quality content from your friends, downloading videos from Instagram is as easy as pie. Just choose one of the methods below and get cracking.
1. Video Downloader for Instagram
Available on: Android
Android users can find an abundance of specialist apps for downloading Instagram videos in the Google Play Store (tips for using the Google Play Store).
One of the most popular is Video Downloader for Instagram. It lets you download or repost videos from Instagram with a single tap. The app can even download the tags that accompany the videos.
The downloaded content is automatically added to your phone’s gallery app.
Download: Video Downloader for Instagram (Free)
2. IFTTT
Available on: Android, iOS, Web
Do you want to download all of your Instagram videos? Or maybe save Instagram videos you like? You can set up an IFTTT applet. To get the applet working, you will need an IFTTT account, an Instagram account, and a Dropbox account (how to get more done with Dropbox).
The result is an automatic process in which any Instagram video you add or like is automatically downloaded and added to your chosen Dropbox folder. What could be simpler than that?
3. PostGraber
Available on: Web
PostGraber differs from a lot of the other web-based Instagram download tools. Whereas most of them can only grab one piece of content per post, PostGraber can download all of the photos and videos that are associated with a single post.
All you need is the URL of the Instagram post you want to download. You can get it on the mobile app by going to Copy Link, or from the browser’s address bar on the web app.
Paste the URL into the box on the PostGraber website and click Go. The web app will take care of the rest.
Note: This app only works with public Instagram posts.
4. Dredown
Available on: Web
Dredown—which is still sometimes referred to by its previous name, Instadown—is one of the original Instagram video download tools, and it’s still going strong.
Like PostGraber, all Dredown needs to work is a URL. Paste the URL into the box and click Dredown. Within a few seconds, your browser will start downloading the MP4 file.
Dredown works with more services than just Instagram. You can also use it to download content from YouTube, Facebook, Keek, Twitter, Twitch, Vine, Vimeo, Metacafe, Vevo, Kohtakte, and Tumblr. For all the services it supports, you just need to URL of the post, video, or photo you want to save.
5. Regrammer
Available on: iOS
Okay, so we’ve covered Android and web apps. But how do you download Instagram videos on iOS?
Well, there are several apps in the App Store that profess the ability to download videos—but they’re often packed with ads and in-app purchases, and are difficult to use.
One exception is Regrammer. The app is entirely free, and although it’s ad-supported, the ads aren’t so obnoxious you’ll want to steer clear.
Once again, you’ll need the URL of the Instagram video you want to download to make the app work. When you have it, open the Regrammer app, paste in the URL, and click Preview.
On the final page, you can choose to either download the video onto your device or repost it under your own name.
Download: Regrammer (Free)
6. OG Instagram
Available on: Android
OG Instagram is not in the Google Play Store. To get your hands on it you’ll need to sideload the app on your Android device.
The app is not just a way to download and save Instagram videos on Android—it’s also a full-featured Instagram client that lets you follow hashtags, use two accounts on the same device, view the profile picture of users (by long-pressing), and share URLs to external apps.
Download: OG Instagram (Free)
7. Gramblast
Available on: Web
We will leave you with one more web app. It’s always sensible to keep a few web apps for downloading Instagram videos in your arsenal, as they will often go down for a couple of days at a time.
By now, you’ll be familiar with the process for using the service. Grab the URL of the video or picture you want, then paste it into the Gramblast web app and click Download.
Depending on the size of the file, you should have a new MP4 on your computer within a matter of seconds. You can use the video to re-upload to a different social network, or just keep it on your hard drive so you can refer back to it later.
Remember Instagram Video Copyrights
As easy as it is to download videos off Instagram, don’t forget that you have no rights over videos you did not create.
Yes, you can download them. Yes, you can enjoy them. But don’t go uploading them as your own, or distributing them in any other way, especially without giving due credit. You wouldn’t want the same thing done to you.
Other Ways to Download Instagram Videos
If these seven apps don’t give the results you want to download videos from Instagram, there are some additional methods you can use.
For example, you can one of the generic apps that let you download streaming videos from websites. VideoGrabby, Video DownloadHelper, and Freemake Video Downloader are all solid options in this department.
Read the full article: 7 Ways to Download Videos From Instagram
Read Full Article
When Is the Safest Time to Invest in Cryptocurrency?

Never.
There will always be a measure of risk when “investing” in Bitcoin, Ethereum, or any other cryptocurrency. However, that risk can be managed.
In this article, we’ll cover the fundamental points you need to know to make a risk-managed investment in cryptocurrency. But a word of warning: do NOT mistake “risk-managed” for “safe” because they are NOT the same thing. Keep reading to find out why.
How Cryptocurrency Investments Work
As with all things traded, digital coins are subject to supply and demand. At any given moment, there are people who have coins and want to sell them (supply) and there are people who want coins and are willing to buy them (demand). Combined, they comprise the coin market.
But not everyone agrees on the value of a coin. Every seller has a minimum price at which they’re willing to sell, and every buyer has a maximum price at which they’re willing to buy.
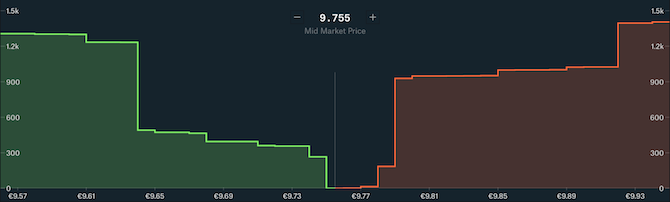
Sellers put their coins on the market at their willing prices, and prospective buyers buy them if the prices are low enough. As lower-priced coins are bought up, only the higher-priced coins remain on the market. As the price goes up, the number of willing buyers diminishes—and if buyers run out, sellers may need to start selling at lower prices. Thus, the price of a coin goes up and down as buyers and sellers enter and leave the market.
The current market price of a specific cryptocurrency is the price of the most recently sold coin.
So how do people make money with cryptocurrency? They buy in at a certain price, wait for the market price to rise, then sell for a profit. However, if the market price never rises above their buy-in price, then selling at a loss is the only option.
In this way, coin investing is similar to stock trading: each coin of a cryptocurrency is like a share in a publicly-traded company, and both coin prices and stock prices are determined by what buyers are willing to spend.
Why Cryptocurrency Investments Are Risky
A coin’s value is tied to how much faith people have in it.
If people really believe that a given crypto project is the future, then they’ll jump aboard the wagon: former non-buyers become buyers, and current buyers become willing to spend more to acquire coins. Sellers become emboldened to hold for the future and become less willing to sell at lower prices. The coin’s price shoots up.
Conversely, if people lose faith and stop believing in the longevity of a coin, then buyers back out and disappear. Sellers lose hope that their coins will be worth anything in the future, so they decide to dump—but they aren’t the only ones. Everyone ends up undercutting each other to offload their coins as fast as possible. The coin’s price plummets.
The problem is, increasing faith in a cryptocurrency is extremely difficult, and even hard-earned faith can evaporate overnight.
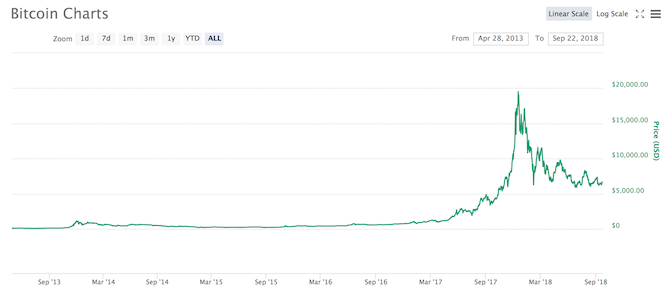
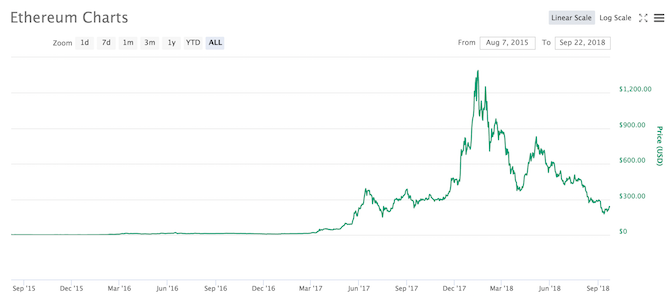
You’ve probably heard that you “need” to invest in cryptocurrencies “while you still can.” Buy now while the price is low so that you can sell when the price shoots back up! And based on the above price-over-time charts, you might be tempted to sink your savings into them. After all, look at those spikes!
If you had invested $1,000 into Bitcoin in January 2017, it would’ve been worth $18,000 in January 2018. If you had invested that same $1,000 into Ethereum in January 2017, it would’ve been worth a whopping $100,000. In just one year! You won’t find that kind of annual return anywhere else.
But high returns come with high risks.
January 2018 saw a huge price rally for nearly every cryptocurrency. If you bought in at these highs, you would have had a very worrying 2018, as the prices subsequently plummeted.
Spikes like this are common in the cryptocurrency world. As of this writing, CoinMarketCap shows over 1,900 different actively-traded cryptocurrencies, many of which experienced their own big spikes similar to what Bitcoin and Ethereum have gone through.
How did these cryptocurrencies fare?
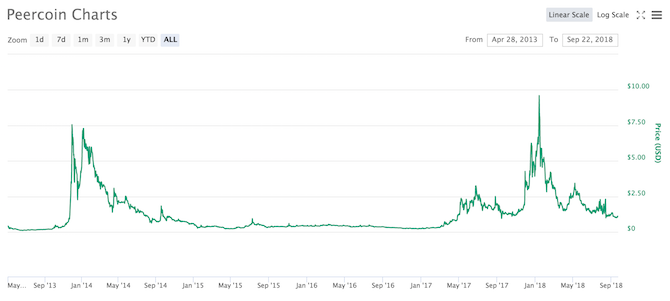
Peercoin became big around the end of 2013, skyrocketing in price through the first quarter of 2014 before users lost faith. The price dwindled down and down, with a few hopeful spikes along the way. The price spiked again in January 2018, when the whole market rocketed, but Peercoin failed to sustain this momentum and dwindled once again.
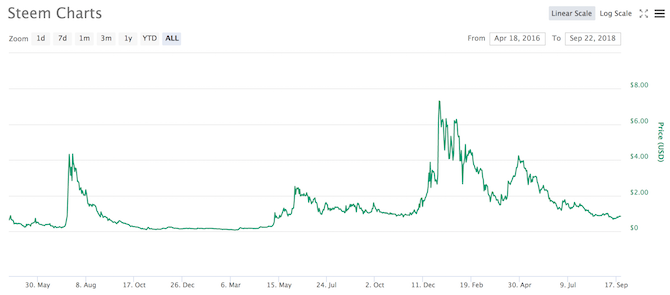
Steem is a younger cryptocurrency, just over two years old as of this writing, that exhibits much of the same patterns as older cryptocurrencies: the price sits stagnant for a quite, a spike comes along, users jump on the wagon, realize the hype wave is over, then sell out before the price plummets. Spikes happened in 2017 and 2018, but none have had a lasting impact on the price.
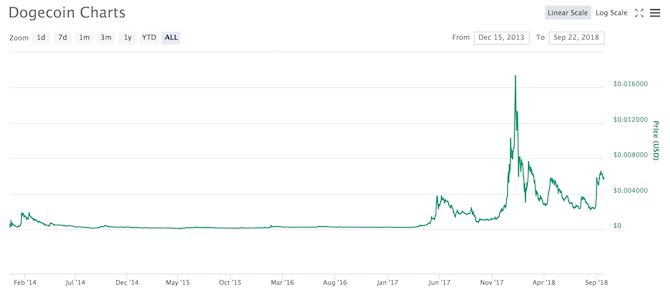
The same thing happened with Dogecoin, which was once the third-largest cryptocurrency in 2014 but is now barely hanging on in the Top 20. Dogecoin is one of the rare examples of a cryptocurrency that spiked to a higher price later in its life, but note how quickly that spike dissipates: it plummets, spikes again, then loses most of its gains within two months.
And that’s the big risk with cryptocurrency investments: you can get rich overnight, but you can also lose it all overnight. Don’t think of it as an investment—it’s a gamble.
Cryptocurrency investment is a game of spikes. You need to already be in the game by the time a spike arrives in order to ride it up for profits. At the same time, you need to get off that ride before everyone else does, otherwise they’ll run away with the profits and leave you empty-handed.
How is crypto investment different from the stock market?
The main issue is a lack of historical data. Cryptocurrencies debuted with Bitcoin in 2009, which means the crypto market hasn’t even been around for a decade. Enthusiasts look at the 2017 spike in crypto interest as a sign of a healthy future, but there’s just no way to know for sure.
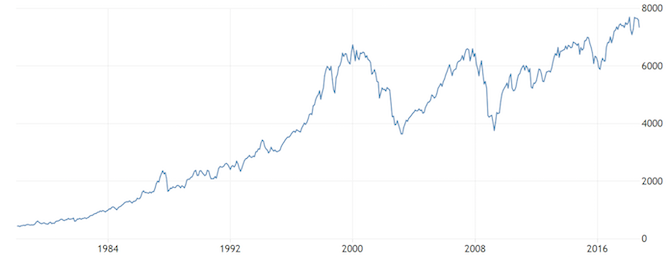
When you look at the US stock market’s history (as shown above), you see all kinds of peaks and valleys, but you also see an upward trend over the long term. We can’t say the same for cryptocurrencies.
Could the US stock market crash and never recover? Sure. It happened to Japan in 1990. But the historical data shows that it’s unlikely. When there’s a crash, you can reasonably hope for a recovery.
There’s no basis for such a hope in cryptocurrency. Could Bitcoin, Ethereum, or any other cryptocurrency soar to higher heights over the next five years? Of course. But could the whole industry collapse and disappear? Absolutely. We simply don’t have enough historical data to do more than guess. It’s still too young and there’s too much uncertainty.
My rule of thumb: if you see a spike in cryptocurrencies, you’ve already missed the hype train. Wait for it to drop, buy in, and hold for another spike—but with the understanding that another spike may never come.
Managing Risk When Investing in Crypto
I’m not saying you shouldn’t invest in cryptocurrencies, but it’s clear that the market is alive and people can still walk away with a killing if they play their cards right.
That being said, here are a few tips to lessen your risk of a total loss:
Don’t put all your eggs in one basket. Don’t stick your entire life savings in cryptocurrency. Unless you’re willing to gamble, crypto shouldn’t be more than 5 percent of your total investment portfolio. And when you do invest in crypto, don’t dump it all into one coin. Diversify between coins that have different missions and different underlying technologies.
Only “invest” money you can afford to lose. Again, cryptocurrencies aren’t really investments—they’re speculations. It’s literally a gamble right now. Expect to lose everything and consider it a bonus if you don’t.
Sell your profits. If you make gains, don’t get greedy. Sell a portion of it to realize profit immediately, then see how the remainder performs. If it goes up again, sell another portion. Don’t “wait for the peak” before you sell—a plunge to zero could wipe you out overnight.
Never store your coins on an exchange. Another Mt. Gox controversy could be right around the corner. Have money on an exchange? Spend it or pull it out. Have coins on an exchange? Transfer them to a cold wallet for secure storage.
Read the full article: When Is the Safest Time to Invest in Cryptocurrency?
Read Full Article
Microsoft Is Ending Support for Skype Classic

Microsoft is preparing to pull support for Skype Classic, officially known as Skype 7.0. Support for the older version of Skype, which has a more classic look and feel to it than the current versions, will end in November on both desktop and mobile.
Microsoft Messes With a Winning Formula
In 2017, Microsoft launched a new version of Skype designed to appeal to a younger demographic. This proved to be rather controversial, as the majority of Skype users are older and not particularly interested in stickers and emojis.
Rather predictably, this led some users to stick with Skype 7.0. In July 2018, Microsoft launched Skype 8.0 and stated that all previous versions would stop working within weeks. Users duly complained, and Microsoft relented. But not for long.
The End Is Nigh for Skype Classic
Microsoft has now announced it will be pulling support for Skype Classic in November. It also added that, “although you may be able to use older versions for a little while, we encourage you to update today to avoid any interruption.”
An update to the original post reads, “As we continue to focus on and improve Skype version 8, support for Skype versions 7, and below will end on November 1, 2018 on desktop devices and November 15, 2018 on mobile and tablet devices.”
To be fair to Microsoft, the company has spent the last year trying to find a happy medium by blending the old and new together. Which meant reintroducing some of the classic features existing users felt were missing from Skype 8.0.
The danger with this approach is ending up with a half-cocked product that no one is particularly happy with. However, Microsoft has now committed to forcing everyone into using the same version of Skype going forward, so we’ll see how that turns out.
There Are Alternatives to Skype…
If you like the way Microsoft has changed Skype recently then upgrade to Skype 8.0 ASAP. But if you’re one of those longterm Skype users who hate the recent changes you might want to consider switching to one of these free Skype alternatives instead.
Read the full article: Microsoft Is Ending Support for Skype Classic
Read Full Article
What Instagram users need to know about Facebook’s security breach
Even if you never log into Facebook itself these days, the other apps and services you use might be impacted by Facebook’s latest big, bad news.
In a follow-up call on Friday’s revelation that Facebook has suffered a security breach affecting at least 50 million accounts, the company clarified that Instagram users were not out of the woods — nor were any other third-party services that utilized Facebook Login. Facebook Login is the tool that allows users to sign in with a Facebook account instead of traditional login credentials and many users choose it as a convenient way to sign into a variety of apps and services.
Third-party apps and sites affected too
Due to the nature of the hack, Facebook cannot rule out the fact that attackers may have also accessed any Instagram account linked to an affected Facebook account through Facebook Login. Still, it’s worth remembering that while Facebook can’t rule it out, the company has no evidence (yet) of this kind of activity.
“So the vulnerability was on Facebook, but these access tokens enable someone to use [a connected account] as if they were the account holder themselves — this does mean they could have access other third party apps that were using Facebook login,” Facebook Vice President of Product Management Guy Rosen explained on the call.
“Now that we have reset all of those access tokens as part of protecting the security of people’s accounts, developers who use Facebook login will be able to detect that those access tokens has been reset, identify those users and as a user, you will simply have to log in again into those third party apps.”
Rosen reiterated that there is plenty Facebook does not know about the hack, including the extent to which attackers manipulated the three security bugs in question to obtain access to external accounts through Facebook Login.
“The vulnerability was on Facebook itself and we’ve yet to determine, given the investigation is really early, [what was] the exact nature of misuse and whether there was any access to Instagram accounts, for example,” Rosen said.
Anyone with a Facebook account affected by the breach — you should have been automatically logged out and will receive a notification — will need to unlink and relink their Instagram account to Facebook in order to continue cross-posting content to Facebook.
How to relink your Facebook account and do a security check
To do relink your Instagram account to Facebook, if you choose to, open Instagram Settings > Linked Accounts and select the checkbox next to Facebook. Click Unlink and confirm your selection. If you’d like to reconnect Instagram with Facebook, you’ll need to select Facebook in the Linked Accounts menu and login with your credentials like normal.
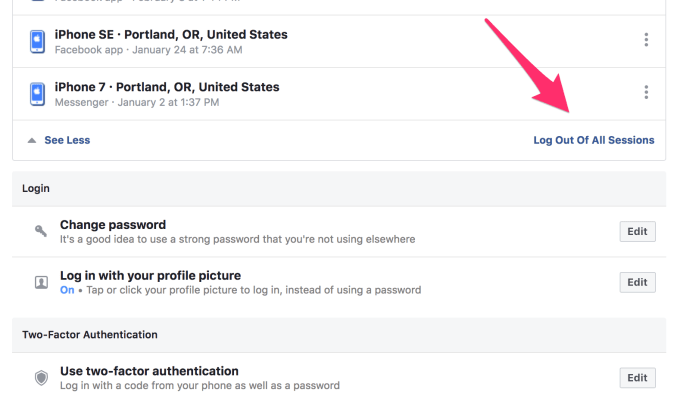
If you know your Facebook account was affected by the breach, it’s wise to check for suspicious activity on your account. You can do this on Facebook through the Security and Login menu.
There, you’ll want to browse the activity listed to make sure you don’t see anything that doesn’t look like you — logins from other countries, for example. If you’re concerned or just want to play it safe, you can always find the link to “Log Out Of All Sessions” by scrolling toward the bottom of the page.
While we know a little bit more now about Facebook’s biggest security breach to date, there’s still a lot that we don’t. Expect plenty of additional information in the coming days and weeks as Facebook surveys the damage and passes that information along to its users. We’ll do the same.
Read Full Article
Facebook is blocking users from posting some stories about its security breach
Some users are reporting that they are unable to post today’s big story about a security breach affecting 50 million Facebook users. The issue appears to only affect particular stories from certain outlets, at this time one story from The Guardian and one from the Associated Press, both reputable press outlets.
Facebook is preventing users from posting The Guardian's report on the Facebook data breach. Ouch. https://t.co/IGU685PjdK pic.twitter.com/GGGrKqBZEc
— Jed Bracy (@JedBracy) September 28, 2018
When going to share the story to their news feed, some users, including members of the staff here at TechCrunch who were able to replicate the bug, were met with the following error message which prevented them from sharing the story.
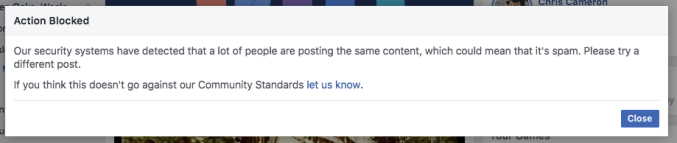
According to the message, Facebook is flagging the stories as spam due to how widely they are being shared or as the message puts it, the system’s observation that “a lot of people are posting the same content.”
To be clear, this isn’t one Facebook content moderator sitting behind a screen rejecting the link somewhere or the company conspiring against users spreading damning news. The situation is another example of Facebook’s automated content flagging tools marking legitimate content as illegitimate, in this case calling it spam. Still, it’s strange and difficult to understand why such a bug wouldn’t affect many other stories that regularly go viral on the social platform.
This instance is by no means a first for Facebook. The platform’s automated tools — which operate at unprecedented scale for a social network — are well known for at times censoring legitimate posts and flagging benign content while failing to detect harassment and hate speech. We’ve reached out to Facebook for details about how this kind of thing happens but the company appears to have its hands full with the bigger news of the day.
While the incident is nothing particularly new, it’s an odd quirk — and in this instance quite a bad look given that the bad news affects Facebook itself.
Read Full Article
5 takeaways on the state of AI from Disrupt SF
The promise of artificial intelligence is immense, but the roadmap to achieving those goals still remains unclear. Onstage at TechCrunch Disrupt SF, some of AI’s leading minds shared their thoughts on current competition in the market, how to ensure algorithms don’t perpetuate racism and the future of human-machine interaction.
Here are five takeaways on the state of AI from Disrupt SF 2018:
1. U.S. companies will face many obstacles if they look to China for AI expansion

Sinnovation CEO Kai-Fu Lee (Photo: TechCrunch/Devin Coldewey)
The meteoric rise in China’s focus on AI has been well-documented and has become impossible to ignore these days. With mega companies like Alibaba and Tencent pouring hundreds of millions of dollars into home-grown businesses, American companies are finding less and less room to navigate and expand in China. AI investor and Sinnovation CEO Kai-Fu Lee described China as living in a “parallel universe” to the U.S. when it comes to AI development.
Sinovation Chairman & CEO Kai-FU Lee says China has surpassed the U.S. in terms of AI capabilities #TCDisrupt pic.twitter.com/r71HlXgDDd
— TechCrunch (@TechCrunch) September 5, 2018
“We should think of it as electricity,” explained Lee, who led Google’s entrance into China. “Thomas Edison and the AI deep learning inventors – who were American – they invented this stuff and then they generously shared it. Now, China, as the largest marketplace with the largest amount of data, is really using AI to find every way to add value to traditional businesses, to internet, to all kinds of spaces.”
“The Chinese entrepreneurial ecosystem is huge so today the most valuable AI companies in computer vision, speech recognition, drones are all Chinese companies.”
2. Bias in AI is a new face on an old problem

SAN FRANCISCO, CA – SEPTEMBER 07: (L-R) UC Berkeley Professor Ken Goldberg, Google AI Research Scientist Timnit Gebru, UCOT Founder and CEO Chris Ategeka, and moderator Devin Coldewey speak onstage during Day 3 of TechCrunch Disrupt SF 2018 at Moscone Center on September 7, 2018 in San Francisco, California. (Photo by Kimberly White/Getty Images for TechCrunch)
AI promises to increase human productivity and efficiency by taking the grunt work out of many processes. But the data used to train many AI systems often falls victim to the same biases of humans and, if unchecked, can further marginalize communities caught up in systemic issues like income disparity and racism.
“People in lower socio-economic statuses are under more surveillance and go through algorithms more,” said Google AI’s Timnit Gebru. “So if they apply for a job that’s lower status they are likely to go through automated tools. We’re right now in a stage where these algorithms are being used in different places and we’re not event checking if they’re breaking existing laws like the Equal Opportunity Act.”
Algorithmic bias is a new face of an old problem rooted in income disparity and racism. Timnit Gebru (Google AI), Ken Goldberg (UC Berkeley) and Chris Ategeka (UCOT) outline steps to build more objective algorithms in the future. #TCDisrupt pic.twitter.com/XnK422JTL8
— TechCrunch (@TechCrunch) September 20, 2018
A potential solution to prevent the spread of toxic algorithms was outlined by UC Berkeley’s Ken Goldberg who cited the concept of ensemble theory, which involves multiple algorithms with various classifiers working together to produce a single result.
We’re right now in a stage where these algorithms are being used in different places and we’re not even checking if they’re breaking existing laws.
But how do we know if the solution to inadequate tech is more tech? Goldberg says this is where having individuals from multiple backgrounds, both in and outside the world of AI, is vital to developing just algorithms. “It’s very relevant to think about both machine intelligence and human intelligence,” explained Goldberg. “Having people with different viewpoints is extremely valuable and I think that’s starting to be recognized by people in business… it’s not because of PR, it’s actually because it will give you better decisions if you get people with different cognitive, diverse viewpoints.”
3. The future of autonomous travel will rely on humans and machines working together

Uber CEO Dara Khosrowshahi (Photo: TechCrunch/Devin Coldewey)
Transportation companies often paint a flowery picture of the near future where mobility will become so automated that human intervention will be detrimental to the process.
That’s not the case, according to Uber CEO Dara Khosrowshahi. In an era that’s racing to put humans on the sidelines, Khosrowshahi says humans and machines working hand-in-hand is the real thing.
“People and computers actually work better than each of them work on a stand-alone basis and we are having the capability of bringing in autonomous technology, third-party technology, Lime, our own product all together to create a hybrid,” said Khosrowshahi.
The future of autonomous travel will rely on people and computers working together, says Uber CEO Dara Khosrowshahi #TCDisrupt pic.twitter.com/K5668OtRXi
— TechCrunch (@TechCrunch) September 6, 2018
Khosrowshahi ultimately envisions the future of Uber being made up of engineers monitoring routes that present the least amount of danger for riders and selecting optimal autonomous routes for passengers. The combination of these two systems will be vital in the maturation of autonomous travel, while also keeping passengers safe in the process.
4. There’s no agreed definition of what makes an algorithm “fair”

SAN FRANCISCO, CA – SEPTEMBER 07: Human Rights Data Analysis Group Lead Statistician Kristian Lum speaks onstage during Day 3 of TechCrunch Disrupt SF 2018 at Moscone Center on September 7, 2018 in San Francisco, California. (Photo by Kimberly White/Getty Images for TechCrunch)
Last July ProPublica released a report highlighting how machine learning can falsely develop its own biases. The investigation examined an AI system used in Fort Lauderdale, Fla., that falsely flagged black defendants as future criminals at a rate twice that of white defendants. These landmark findings set off a wave of conversation on the ingredients needed to build a fair algorithms.
One year later AI experts still don’t have the recipe fully developed, but many agree a contextual approach that combines mathematics and an understanding of human subjects in an algorithm is the best path forward.
How can we create fair algorithms? Kristian Lum (Human Rights Data Analysis Group) says there’s no clear answer, but it depends on the contextual data training the AI #TCDisrupt pic.twitter.com/CEiglgeX2d
— TechCrunch (@TechCrunch) September 19, 2018
“Unfortunately there is not a universally agreed upon definition of what fairness looks like,” said Kristian Lum, lead statistician at the Human Rights Data Analysis Group. “How you slice and dice the data can determine whether you ultimately decide the algorithm is unfair.”
Lum goes on to explain that research in the past few years has revolved around exploring the mathematical definition of fairness, but this approach is often incompatible to the moral outlook on AI.
“What makes an algorithm fair is highly contextually dependent, and it’s going to depend so much on the training data that’s going into it,” said Lum. “You’re going to have to understand a lot about the problem, you’re going to have to understand a lot about the data, and even when that happens there will still be disagreements on the mathematical definitions of fairness.”
5. AI and Zero Trust are a “marriage made in heaven” and will be key in the evolution of cybersecurity

SAN FRANCISCO, CA – SEPTEMBER 06: (l-R) Duo VP of Security Mike Hanley, Okta Executive Director of Cybersecurity Marc Rogers, and moderator Mike Butcher speak onstage during Day 2 of TechCrunch Disrupt SF 2018 at Moscone Center on September 6, 2018 in San Francisco, California. (Photo by Kimberly White/Getty Images for TechCrunch)
If previous elections have taught us anything it’s that security systems are in dire need of improvement to protect personal data, financial assets and the foundation of democracy itself. Facebook’s ex-chief security officer Alex Stamos shared a grim outlook on the current state of politics and cybersecurity at Disrupt SF, stating the security infrastructure for the upcoming Midterm elections isn’t much better than it was in 2016.
So how effective will AI be in improving these systems? Marc Rodgers of Okta and Mike Hanley of Duo Security believe the combination of AI and a security model called Zero Trust, which cuts off all users from accessing a system until they can prove themselves, are the key to developing security systems that actively fight off breaches without the assistance of humans.
Marc Rodgers (Okta) and Mike Hanley (Duo) outline how AI and Zero Trust will work hand-in-hand to build future security systems #TCDisrupt pic.twitter.com/h23e8Kzu2j
— TechCrunch (@TechCrunch) September 25, 2018
“AI and Zero Trust are a marriage made in heaven because the whole idea behind Zero Trust is you design policies that sit inside your network,” said Rodgers. “AI is great at doing human decisions much faster than a human ever can and I have great hope that as Zero Trust evolves, we’re going to see AI baked into the new Zero Trust platforms.”
By handing much of the heavy lifting to machines, cybersecurity professionals will also have the opportunity to solve another pressing issue: being able to staff qualified security experts to manage these systems.
“There’s also a substantial labor shortage of qualified security professionals that can actually do the work needed to be done,” said Hanley. “That creates a tremendous opportunity for security vendors to figure out what are those jobs that need to be done, and there are many unsolved challenges in that space. Policy engines are one of the more interesting ones.”
Read Full Article
Everything you need to know about Facebook’s data breach affecting 50M users
Facebook is cleaning up after a major security incident exposed the account data of millions of users. What’s already been a rocky year after the Cambridge Analytica scandal, the company is scrambling to regain its users trust after another security incident exposed user data.
Here’s everything you need to know so far.
What happened?
Facebook says at least 50 million users’ data may be at risk after attackers exploited a vulnerability that allowed them access to personal data. The company also preventively secure 40 million additional accounts out of an abundance of caution.
What data were the hackers after?
Facebook CEO Mark Zuckerberg said that the company has not seen any accounts compromised and improperly accessed — although it’s early days and that may change. But Zuckerberg said that the attackers were using Facebook developer APIs to obtain some information, like “name, gender, and hometowns” that’s linked to a user’s profile page.
What data wasn’t taken?
Facebook said that it looks unlikely that private messages were accessed. No credit card information was taken in the breach, Facebook said. Again, that may change as the company’s investigation continues.
What’s an access token? Do I need to change my password?
When you enter your username and password on most sites and apps, including Facebook, your browser or device is set an access tokens. This keeps you logged in, without you having to enter your credentials every time you log in. But the token doesn’t store your password — so there’s no need to change your password.
Is this why Facebook logged me out of my account?
Yes, Facebook says it reset the access tokens of all users affected. That means some 90 million users will have been logged out of their account — either on their phone or computer — in the past day. This also includes users on Facebook Messenger.
When did this attack happen?
The vulnerability was introduced on the site in July 2017, but Facebook didn’t know about it until this month, on September 16, 2018, when it spotted unusual activity. That means the hackers could have had access to user data for a long time, as Facebook is not sure right now when the attack began.
Who would do this?
Facebook doesn’t know who attacked the site, but the FBI is investigating, it says.
However, Facebook has in the past found evidence of Russia’s attempts to meddle in American democracy and influence our elections — but it’s not to say that Russia is behind this new attack. Attribution is incredibly difficult and takes a lot of time and effort. It recently took the FBI more than two years to confirm that North Korea was behind the Sony hack in 2016 — so we might be in for a long wait.
How did the attackers get in?
Not one, but three bugs led to the data exposure.
In July 2017, Facebook inadvertently introduced three vulnerabilities in its video uploader, said Guy Rosen, Facebook’s vice president of product management, in a call with reporters. When using the “View As” feature to view your profile as someone else, the video uploader would occasionally appear when it shouldn’t display at all. When it appeared, it generated an access token using the person who the profile page was being viewed as. If that token was obtained, an attacker could log into the account of the other person.
Is the problem fixed?
Facebook says it fixed the vulnerability on September 27, and then began resetting the access tokens of people to protect the security of their accounts.
Will Facebook be fined or punished?
If Facebook is found to have breached European data protection rules — the newly implemented General Data Protection Regulation (GDPR) — the company can face fines of up to four percent of its global revenue.
However, that fine can’t be levied until Facebook knows more about the nature of the breach and the risk to users.
Another data breach of this scale – especially coming in the wake of the Cambridge Analytica scandal and other data leaks – has some in Congress calling for the social network to be regulated. Sen. Mark Warner (D-VA) issued a stern reprimand to Facebook over today’s news, and again pushed his proposal for regulating companies holding large data sets as ““information fiduciaries” with additional consequences for improper security.
FTC Commissioner Rohit Chopra also tweeted that “I want answers” regarding the Facebook hack. It’s reasonable to assume that there could be investigators in both the U.S. and Europe to figure out what happened.
Can I check to see if my account was improperly accessed?
You can. Once you log back into your Facebook account, you can go to your account’s security and login page, which lets you see where you’ve logged in. If you had your access tokens revoked and had to log in again, you should see only the devices that you logged back in with.
Should I delete my Facebook account?
That’s up to you! But you may want to take some precautions like changing your password and turning on two-factor authentication, if you haven’t done so already. If you’re weren’t impacted by this, you may want to take the time to delete some of the personal information you’ve shared to Facebook to reduce your risk of exposure in future attacks, if they were to occur.
Read Full Article
How (Not) to Upgrade to the Latest Windows 10 Version

Windows 10 build 1809 is coming to your PC soon. The official release date is October 2, 2018, but the rollout could take many months. We’ll show you how you can get the latest feature update right now or how to delay it for as long as possible, in case you don’t want to upgrade.
Which Version of Windows Do You Have?
First, find out which version of Windows you’re running right now.
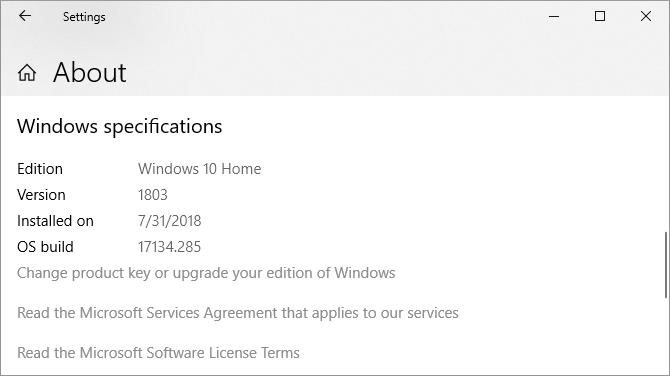
If you’re running Windows 10, go to Start > Settings > System > About and check what it says under Windows Specifications.
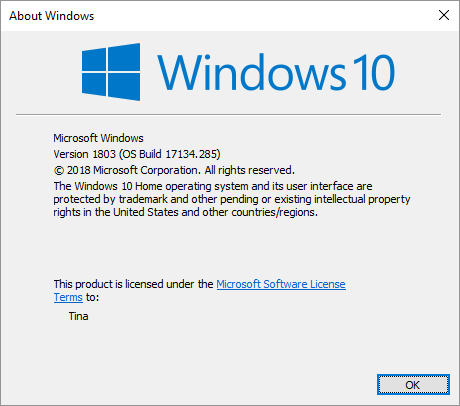
For a quick check that works on any version of Windows, press Windows + Q, type winver, and hit Enter.
If you’re still on Windows 7 or 8, the only way to upgrade to Windows 10 now is to buy a copy and install it. Earlier this year, Microsoft closed the loophole that permitted a free Windows 10 upgrade.
How Not to Upgrade Windows 10
Not upgrading to the latest version of Windows 10 remains a sensible choice. You’ll maximize your time on a stable installation and avoid bugs. Whether you can temporarily delay the Windows 10 October 2018 Update depends on your Windows edition.
Windows 10 Home
As a Home user, you can temporarily disable Windows Update by setting your internet connection to metered.
Go to Start > Settings > Network & Internet > Wi-Fi, select the network you’re connected to, and switch the slider under Set as metered connection to On. This path now also works for Ethernet connections. As soon as you connect to an unmetered Wi-Fi or LAN network, Windows Update will start downloading updates again.
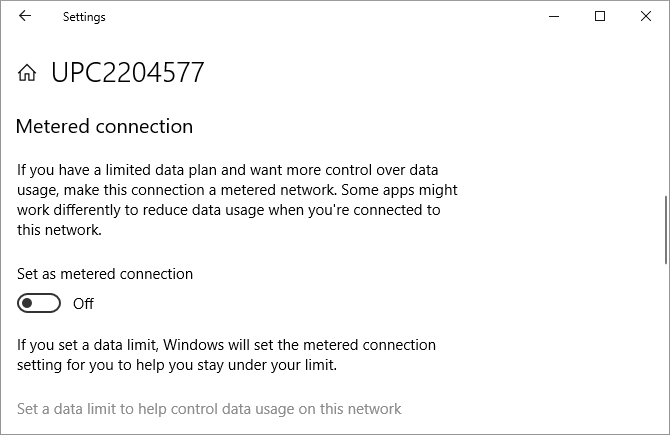
Unfortunately, this is just a temporary workaround. Though it could take many weeks, you should prepare for the impending upgrade that Windows Update will eventually drop on you.
Windows 10 Pro, Education, and Business
If you’re on one of these Windows 10 editions, you have the luxury of temporarily deferring feature updates.
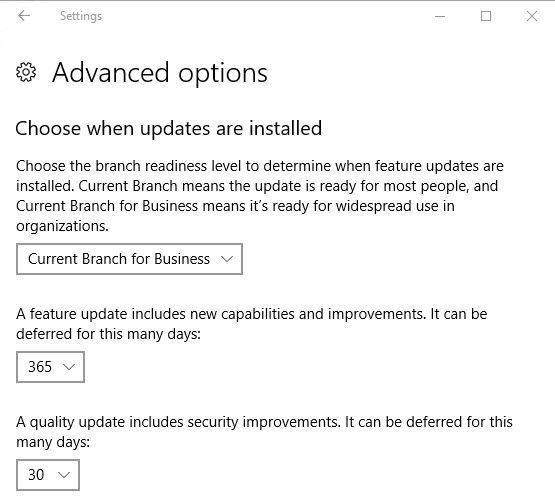
To pause updates completely for up to 35 days, head to Settings > Update & Security > Windows Update > Advanced options and under Pause Updates, move the slider into the On position. Note that once updates resume, you will have to install the latest updates before you can pause Windows Update again.
To defer updates, stay in the Advanced options window. Under Choose when updates are installed, select for how many days you want to defer the feature update; the maximum is 365 days. Unless you don’t want to receive security updates, select zero days for quality updates.
Did the update download, but you’re not ready to install, yet? You can postpone it once more for one week. Go to Settings > Update & Security > Windows Update and select Restart options. Here you can schedule a time and date for the pending update, up to 7 days in the future.
Preparing Your Windows 10 Upgrade
To upgrade to the October 2018 Update, you should be on version 1803, also known as the April 2018 Update. If that’s your Windows version, you’re good to go. Before you upgrade, however, check off these pre-installation To-Dos:
-
Create a Windows recovery drive.
-
Back up your product keys.
-
Enable System Restore.
-
Back up your important data.
With Windows, you never know what could go wrong. So be prepared and do your Windows housekeeping. You’ll find detailed instructions in our article on what to do before you upgrade to the Windows 10 Fall Creators Update.
The Latest Builds: Become a Windows Insider
As Windows Insider, you’ll always run the latest Windows 10 builds. It’s the fast lane to new features, but you also risk facing countless bugs and problems with the operating system. Are you up for the challenge?
How to Join the Windows Insider Program
To become a Windows Insider, you have to go through the following steps:
- Sign up for the Windows Insider Program. You’ll need a Microsoft account.
- Make sure you sign into Windows using your Microsoft account: Go to Start > Settings > Accounts > Your info to change how you sign in.
- Enroll your Windows 10 computer: Go to Start > Settings > Update & Seurity > Windows Insider Program > Get started to opt in.
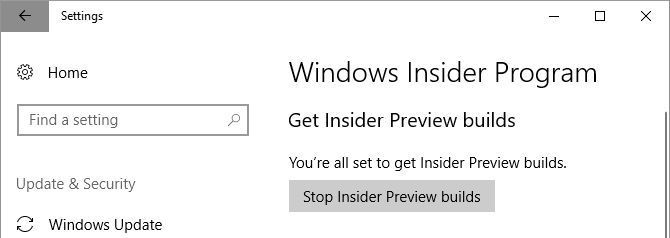
You’ll have to link your Microsoft account and choose a Windows Update branch. We recommend the slow ring.
Twice a year, when the Windows Insider build aligns with the latest build that Microsoft is rolling out to the public (the RTM build), you’ll be able to exit the Insider program without having to reinstall. When that’s the case, head to Start > Settings > Update & Security > Windows Insider Program and click Stop Insider Preview builds.
The Latest Stable Release of Windows 10
Being a Windows Insider means you’ll often run buggy versions of Windows 10. The safe choice is to wait for a stable release of Windows 10 and use one of the following upgrade routes.
Upgrade to Windows 10 Version 1809 via Windows Update
When your computer is ready to upgrade, you’ll receive the October 2018 Update through Windows Update. It’s worth being patient. If Microsoft doesn’t have reliable data for your hardware or if Insiders with your specs experienced lots of issues, the update may not roll out to your system for some time.
To check whether you’re ready to upgrade, head to Start > Settings > Update & Security > Windows Update and click Check for updates. Once the upgrade has downloaded, you’ll see it listed here.
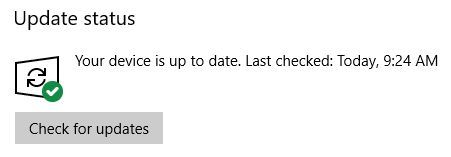
Before you can upgrade to a new build, however, you’ll have to install any pending security updates. Make sure you didn’t pause or defer feature updates under Advanced options.
Manually Install Windows 10 Using the Media Creation Tool
If Windows Update doesn’t think it’s your turn yet, you can force the upgrade using Microsoft’s Windows 10 Media Creation Tool (open this link in Microsoft Edge).
You can click the Update now link to launch the Update Assistant and initiate the upgrade directly from the website.
Or click Download tool now to prepare Windows 10 installation media for a clean install.
Please refer to the article linked in the previous paragraph for a step-by-step guide to using the Windows 10 Media Creation tool.
Should You Upgrade Windows 10?
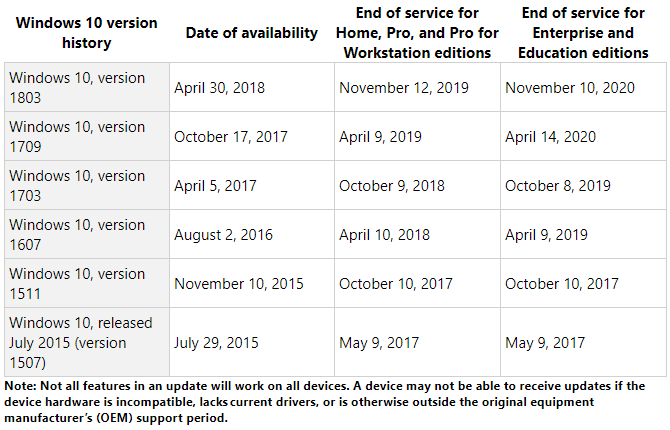
It depends on which version of Windows you’re currently using. Generally, Microsoft will stop supporting each Windows 10 version 18 months after its initial release.
Windows 10 Home, Version 1709 or 1803
You should wait until the upgrade is available through Windows Update. And even then, it’s safer to defer the feature update and wait a little longer until Microsoft has fixed common bugs. Although you can roll back to your previous Windows version for 10 days (previously 30 days), it’s not worth the hassle.
Moreover, if you’re presently running the Windows 10 Fall Creators or April 2018 Update, you’ll continue to receive security patches until April or November 2019, respectively. There’s no rush to update right now, so take your time.
Older Windows 10 Home Versions
The only time you should upgrade is when support for your current Windows 10 version ends. But this won’t happen for many years.
The original Windows 10 release, version 1507, as well as versions 1511 (Fall Update), 1607 (Anniversary Update), and 1703 (Creators Update) have all reached their end of service. If you’re still running one of these versions, you’re no longer receiving security patches and should upgrade immediately.
If your machine supports the October 2018 Update and you’re on a Windows 10 version prior to 1803, we’d recommend waiting for the release of the latest feature update and then upgrading manually using the Windows Media Creation Tool, as described above.
Should you be stuck on an older version because your machine can’t upgrade, there’s a silver lining! For systems that see a “Windows 10 is no longer supported on this PC” error while trying to upgrade, Microsoft has extended support until 2023.
Microsoft introduced this exception for PCs using Intel’s Clover Trail processor, but it might extend to other unsupported hardware as well.
“To keep our customers secure, we will provide security updates to these specific devices running the Windows 10 Anniversary Update until January of 2023, which aligns with the original Windows 8.1 extended support period.”
Windows 10 Enterprise and Education Editions
Windows 10 Enterprise and Education users can add an additional six months to the dates above. Earlier this year, Microsoft said:
“Windows 10 version 1511, 1607, 1703 and 1709 will continue to receive monthly servicing updates at no-cost for a period of 6 months past the end of service dates. The security-only updates are available through all normal channels including: Windows Update (WU/WUfB), WSUS, the Update Catalog, and enterprise management solutions and are delivered as standard cumulative update packages.”
And:
“Some versions of Enterprise and Education editions will have an option for an additional paid extension for eligible volume licensing customers. Customers should reach out to their Microsoft account team for more information about a paid program.”
Welcome to the Future of Windows
The good news is that the latest Windows 10 version will hijack your computer for only around 30 minutes. Microsoft has optimized the installation process and enabled many installation steps to run in the background. This means you can continue to use your machine for a lot longer before you have to restart.
Once you’ve successfully upgraded to the Windows 10 October Update, double-check all your privacy-related settings and restore your preferences. You might also want to set up or disable new features.
Read the full article: How (Not) to Upgrade to the Latest Windows 10 Version
Read Full Article