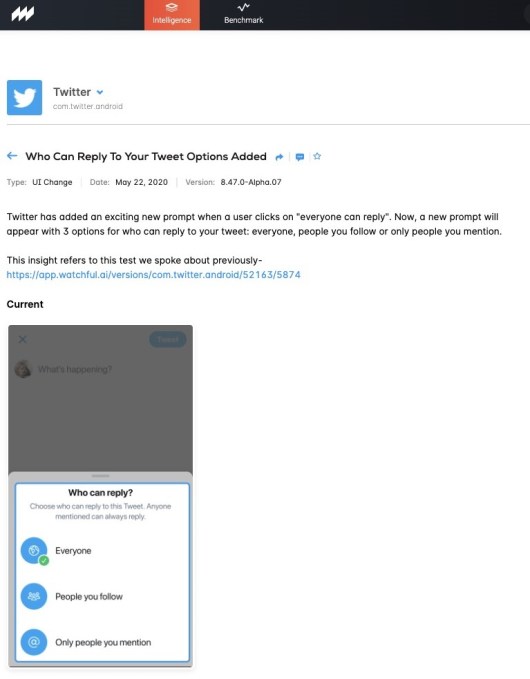
Most people interested in privacy or who stream Netflix need a VPN. You might only need it for your browser. Or you could require a full-VPN service to protect all your internet traffic. But what’s the right solution for your privacy concerns? CactusVPN offers most of what users need.
Is CactusVPN Right for You?
Subscribing to a virtual private network (VPN) means you can protect your privacy, particularly when using public Wi-Fi. It can also block electronic surveillance, and potentially frustrate advertising. A VPN can also protect against ISP throttling and geo-location blocking, if you ever need Netflix from another country (or if you want American Netflix). But all that is not the same thing as security from surveillance.
No VPN will protect you from physical surveillance. Members of your household can monitor internet activity regardless of whether you use a VPN. A VPN is designed more for domestic users than anyone else. Political journalists, dissidents, freedom fighters, and anyone wishing to learn restricted information publicly available elsewhere in the world should only rely on a VPN in conjunction with encrypted messaging (e.g. Signal) or accessing the internet via Tor.
However, if you’re comfortable with the inherent limitations of all VPN technology, CactusVPN offers relatively inexpensive plans ranging in price from $3.20 for the full package or as low as $2.27 for a less private way to bypass streaming geo-restrictions on Netflix.
Is Your Subscription Safe With CactusVPN?
Being able to trust your VPN is vital. If there is no trust, there is no point in using the service. The idea that a VPN might take your money and run, provide a substandard service, renege on its guarantees and features, and even share your logs with a third party, should be enough to make you look elsewhere.
According to their About page, CactusVPN was formed by three friends in 2011 and operates 27 high-speed VPN servers across 15 countries. Its headquarters is in Moldova (in Eastern Europe).
![]()
Moldova is not a member of the European Union so it is not under any existing or future data-sharing obligation. Similarly, it is not a Five Eyes group (FVEY) member, so there is no legal requirement for CactusVPN to share data with Anglo-sphere security services.
The CactusVPN philosophy is simple:
We believe everyone deserves privacy and freedom, we believe internet should be safe for everyone; we believe people shouldn’t be afraid of using the internet.
CactusVPN Free vs. Pro Features
To give you the full CactusVPN experience, both the free and pro (or paid) versions of the app include the same features. While the VPN service is wise to provide this, 24 hours probably isn’t long enough to fully appreciate any service.
The following features are all available in both CactusVPN free and pro modes.
Internet Kill Switch
A vital feature found in all good VPN clients, an internet kill switch cuts access if the VPN connection drops. A lot of different causes can cause a VPN to suddenly cut out. And most computers are designed to reestablish an internet connection as soon as the VPN drops. Without a kill switch, this automatically exposes your location to a variety of sources.
A kill switch in theory blocks all connection after a VPN drops. This means all internet is blocked until you manually reconnect to the VPN or close the client.
CactusVPN’s Apps Killer
CactusVPN, aside from offering a dedicated kill switch, offers a feature called “Apps Killer”. Apps Killer prevents only certain apps, that you select, from connecting to the internet. One scenario is blocking access to the internet during a DDoS attack on an online game. Meanwhile, if you’re torrenting with CactusVPN, Apps Killer will close your torrent client if the VPN connection goes down. This will conceal torrenting activity from your ISP, even in the event of a VPN outage. In theory, at least.
In practice, a kill switch is just another layer of identity protection.
Sort Servers by Speed
Need to find the fastest server? Like many VPN clients, CactusVPN has a drop-down menu to choose from the library of servers. While this is sorted by location by default, the list can be reorganized to Sort by speed. It’s a useful feature which we hope other VPNs will introduce.
![]()
Note that whatever server you choose will be affected by the basic speed of your internet connection. See below for speed testing results.
Easy Server Switching
As stated, the server can be easily switched to any other location. This is again via the drop-down menu, where the new server (in any city or country) can be selected. A short wait is needed while the VPN reconnects.
Easy VPN Protocol Switching
VPN protocol switching is also a feature, although this can only be done between connections. SSTP, OpenVPN, L2TP, PPTP, and IKEv2 protocols are all available via the Settings screen. We’ve written about the various advantages of VPN protocols, such as OpenVPN vs. IPSec and SSTP.
![]()
DNS Leak protection
Also in the settings screen is the option to enable DNS leak protection. Three servers can be used here: CactusVPN DNS, Google DNS, and OpenDNS.
DNS leakage has been a major problem for VPN services over the years. Having leak protection is always an advantage, but it’s curious to see it disabled by default. It may be that the service provider has disabled leak protection in order to improve VPN reliability. After all, many browsers can be manually set to prevent WebRTC leaks—at the cost of website compatibility.
Smart DNS
![]()
An alternative mode is bundled with CactusVPN: Smart DNS. This is an alternative to a VPN, intended to enable region-blocked streaming without the load of VPN encryption and other VPN features. Intended for streaming video, it’s ideal for viewing Netflix on CactusVPN.
VPN Apps for All OSes
CactusVPN offers apps for Windows, macOS, iOS, Android and Android TV, Fire TV, and extensions for Chrome and Firefox browsers. As such, you should be able to use the service on all your devices. There is also support for other hardware via OpenVPN.
For the Fire Stick, CactusVPN offers a (free for 24 hours) VPN app.
Download: CactusVPN for the Fire Stick (24-Hours Free)
Money Back Guarantee
On top of it all, CactusVPN offers disappointed customers their money back.
Its money-back guarantee comes into play if you’re unable to connect to the CactusVPN VPN or Smart DNS servers. This is a 30-day refund policy acts like a parachute if you subscribe after trying the CactusVPN free version.
CactusVPN Security and Privacy
An insecure VPN is of no use whatsoever. Knowing the strength of security and privacy before buying a subscription is a huge advantage. Fortunately, CactusVPN’s free option can prove advantageous here.
Shared IP Address
This is a useful security feature that prevents activity being traced to your device. Instead, a shared IP address is used, grouping CactusVPN users together.
Encryption
CactusVPN employs an interesting approach to encryption, utilizing both 128- and 256-bit AES encryption. While this might seem archaic, their reasoning is compelling:
The AES-128 is very strong and it cannot be cracked through full-scale search on the key. Although you may be entitled to think that longer keys offer more security benefits, the truth is that an algorithm can’t be ‘less broken’ than ‘not broken’. So there is no additional benefit for security from cranking up the key size to 256 bits.
In addition, CactusVPN highlights that a 256-bit AES connection will use 40% more CPU. As such, their argument is that there are computer resource trade-offs between security and computational overhead.
Meanwhile, several VPN protocols are on offer with CactusVPN: SSTP, L2TP/IPSec, OpenVPN, IKEv2/IPSec, SoftEther and PPTP. Which option is best depends on your activity. Overall, OpenVPN is perhaps the most desirable, but not always practical to set up. CactusVPN recommends OpenVPN and SoftEther for torrenting, however, and OpenVPN for security.
Logging Policy
A major concern for privacy advocates using VPNs is the logging policy (as with warrant canaries, we are agnostic about the realities of logging policies). Is the data of customer activity available to third parties?
CactusVPN has a “guaranteed no-logs policy” which they hope will generate trust. Their policy states:
…we will not store any data relating to your activities while using any of our privacy solutions, and will not record, monitor, log or store any of your information. CactusVPN also guarantees that none of your information will be passed on to a third party.
In addition, they do not store “…any IP addresses, traffic logs, connection timestamps, used bandwidth or session duration information that could be traced to a single person.”
In truth, logging policies are not very enforceable outside the legal jurisdiction in which the host company resides. They are generally designed to protect the host company against consumer violations of said policy, not the customer.
CactusVPN Speed Test
A VPN reduces the speed of your internet connection—sometimes a lot. So, it’s worth knowing in advance just how much the speed will be lost.
We’ve tested CactusVPN with premium speed-testing service Speedtest.net. Note that this test was performed on a broadband fiber FTTC (Fiber to the Cabinet) local loop.
First, the speed test without CactusVPN connected:
![]()
As you can see, the speed is 41.47Mbps down, 10.05Mbps up, with a ping of 14 meters per second.
Via a VPN server in London:
![]()
39.63Mbps down, 9.57Mbps up, 17 m/s.
Finally, a CactusVPN server in Zurich, Switzerland:
![]()
Notice the difference in ping rate: 39.33Mbps down, 9.29Mbps up, a ping of 43 milliseconds.
So, with local servers, the CactusVPN speed is good, although ping rate (understandably) degrades with distance.
Smart DNS Speed Test
In addition to testing the speed of the CactusVPN, we also looked at speed using the Smart DNS feature. After all, there’s no point advertising a fast alternative to VPN for video streaming if it isn’t fast enough.
With the Smart DNS mode enabled, the results are:
![]()
As you can see, the result is a 39.23Mbps download, and 10.09Mbps upload score. Ping is 14 milliseconds to a DNS server around 40 miles (64.37 km) away.
CactusVPN Customer Service Options
Several support options are available from CactusVPN. Foremost among these is the Submit ticket option in the client app. Available alongside a Save logs button, both are found in the Help screen (a doctor’s bag in the top-left corner), accompanied by links for the ToS, Blog, Refund Policy, and more.
Clicking Submit ticket opens the relevant page on the CactusVPN website, saving you time looking for the link. Note that all contact with CactusVPN is via the support ticket screen. While they operate social media accounts (such as @CactusVPN on Twitter) the response will always be to raise a support ticket.
You can also start a live chat during business hours. This will typically appear unprompted while you browse the site.
The Support tab on the website, meanwhile, features a collection of tutorials, an FAQ, and other guided sections.
Should You Subscribe to CactusVPN?
With all of this considered, you should be ready to decide: CactusVPN, or another service?
Overall, we found it a competent VPN service. While the Windows client crashed on one occasion while switching protocols, it was otherwise stable. It’s ideal for most activities: CactusVPN connects to Netflix libraries around the world without any problem; you can use Cactus VPN servers for torrenting. CactusVPN is also safe to use for online shopping and protecting your device on public Wi-Fi.
General usage for browsing yielded good results. However, one incident caused concern: a visit to this very site via the CactusVPN server in Kansas, USA. The resulting web page was a “520 Web server is returning an unknown error”, which didn’t occur when browsing VPN Proof normally. This appears to be a common issue with free VPNs, a good reason for avoiding them. Of course, CactusVPN is not a free VPN, but might need to take steps to avoid 520 errors.
For privacy concerns, it offers a mature, considered no-logging policy that should ensure CactusVPN earns your consideration as a VPN option.
On the other hand, not all the features were interesting. While the Smart DNS mode is useful, it’s probably more suited to streaming video through a game console than as an alternative mode on your PC.
Still not certain? Use the CactusVPN free trial to help make your mind up.
Read the full article: CactusVPN Review: Can a Free VPN Option Make It Less Prickly?
Read Full Article