A blog about how-to, internet, social-networks, windows, linux, blogging, tips and tricks.
10 May 2019
India to reportedly investigate Google over alleged Android abuse
More than 95 percent of the smartphones that ship in India run Android operating system, according to industry estimates. Now the Indian antitrust watchdog is convinced that the nation should investigate if Google is abusing the dominant position of its mobile operating system to hurt local rivals.
The Competition Commission of India (CCI), the local antimonopoly regulator, began looking at Google’s Android business in India last year after it received a complaint from unspecified people. In mid-April, the regulator decided that there was merit in the accusations and ordered its investigation unit to conduct a full-investigation, according to a report by Reuters, which cites unnamed sources.
The investigation, not the first of its kind, will take about a year to conclude and could see Google executives be asked to be summoned before the regulator, the news agency reported. We’ve reached out to Google for comment. The CCI has not publicly commented on the probe.
If found guilty, Google may be fined up to 10 percent of its local revenue or 300 percent of its net profits. Even as India has emerged as one of Google’s largest markets, the company makes relatively a tiny amount in the nation. It clocked $1.4 billion in revenue in India in the year that ended in March 2018, according to regulatory filings, compared to over $100 billion it generated globally in a comparable time period.
The specific accusations, as well as identity of those who filed the complaint, remains unclear. In a statement to Reuters, Google said that it was looking forward to working with the CCI to “to demonstrate how Android has led to more competition and innovation, not less.”
With the launch of this investigation, India is joining the EU, which continues to look at several businesses of Google — including Android — to ensure that the company is not abusing its dominant position in the market. Earlier this year, the EU regulators concluded that Google had forced its OEM partners to prebundle a number of apps including Google Search, Chrome browser, and Google Play Store on their Android handsets.
Following the verdict, which Google has appealed, the Android maker announced it will give users more choices for browsers and search engines.
India’s regulator has previously investigated Google’s search business and Apple’s partnerships with local carriers for sale of iPhones. Apple’s iOS has tiny market share in India, where most people have annual income of less than $2,000.
Read Full Article
The 8 Best Linux Password Managers to Stay Secure

Concerns over privacy and security are one of the big reasons people use free and open source software. But today, safeguarding the data on your computer is only part of the challenge. How do we manage all the passwords for all the different accounts we create across the web?
Password managers are a great way to handle the issue. Here are the best Linux password managers you can trust to handle your passwords properly.
1. KeePass

KeePass stores all of your passwords in an encrypted database, which exists within a single file on your computer. You can access this database using a password, a key file, or both.
This database is portable, so you can access your passwords on any device that contains a copy. If you don’t create new accounts often, you can copy this file over manually. Or you can set up whichever Linux-friendly file syncing method works best for you.
KeePass began as a Windows app in 2003, and the interface hasn’t changed much since then. So while the functionality is there, the design can feel a bit long in the tooth. It’s not as intuitive as some of the newer web-based options around. But thanks to the app’s maturity and popularity, there are plenty of plugins that extend what KeePass can do.
There are many versions of KeePass available for Linux. KeePass is a port of the Windows app. KeePassX and KeePassXC are more Linux-friendly alternatives built using the Qt toolkit.
Download: KeePass (Free)
Download: KeePass X (Free)
Download: KeePass XC (Free)
2. GNOME Password Safe

I care a great deal about how well the apps I use integrate with the rest of the desktop environment. If you do too, and you use GNOME, then you know most options don’t fit in all that well. In that case, check out Password Safe.
Password Safe is about as simple as a desktop-based password manager can get. First, you create a safe that contains all of your passwords. Then you choose to protect this safe with a password, a key file, or both. Afterward, you enter your accounts and passwords. If this sounds familiar, that’s because Password Safe uses the same format as KeePass.
Password Safe removes most of the complexity of KeePass and most other options. This makes it a great first password manager for those of us who have never used such software before. On the other hand, you may find the app frustrating if it’s missing features you’ve grown accustomed to elsewhere.
As an added bonus, Password Safe’s interface scales down to fit mobile devices, namely the Purism Librem 5.
Download: GNOME Password Safe (Free)
3. Password Safe

There is an unrelated open source Windows app that also goes by the name Password Safe. A beta version is available for Linux,
Password Safe uses a concept similar to KeePass. You can store passwords and usernames in one or more databases. The app makes sure to prevent sensitive data from swapping to disk, wipes temporary data in memory as quickly as possible, and doesn’t save your master passphrase directly. These are some of the methods password managers keep your passwords safe.
Password Safe is a more desktop agnostic app. It will look more at home on some non-GNOME desktops, such as Xfce and MATE.
Download: Password Safe (Free)
4. Password Gorilla

If you like Password Safe but the beta isn’t working for you, there’s a compatible app that has already been around for years.
Password Gorilla is another cross-platform password manager that stores all of your accounts in one encrypted Password Safe database. Versions of Password Gorilla exist for Windows and macOS. Mobile versions don’t exist, but you can find compatible versions of Password Safe for Android and iOS.
Download: Password Gorilla (Free)
5. qMasterPassword

Don’t like the idea of a single file containing all of your passwords? qMasterPassword offers an alternative approach. This password manager asks you to create a single master password. Then it generates passwords for your accounts using the master password and the relevant website. Even if someone knows you use qMasterPassword, they can’t easily guess your login credentials without knowing the master password you used to generate them.
qMasterPassword is a Linux version of the Master Password algorithm. It is compatible with other implementations of that product, some of which are available for Android and iOS. As Qt-based software, qMasterPassword is a great app to use with KDE Plasma.
Download: qMasterPassword (Free)
6. QtPass

KeePass may be the most established option on this list, but that doesn’t mean it’s the only tool that caters to the more technical among us. Pass is a command line tool that stores each password inside of a separate GPG encrypted file.
Thanks to QtPass, you can adopt the pass approach to security without having to use the terminal. QtPass is a desktop tool that lets you manage your passwords without learning a single command. You can perform most of the same functions as the command-line version.
Download: QtPass (Free)
7. Bitwarden

The aforementioned options all exist offline. Bitwarden is an open source web service that syncs your passwords across all of your PCs and mobile devices. Versions exist for Linux, as well as Android and iOS. The available web browser extensions can also automatically enter stored passwords when you visit a website.
Bitwarden saves your passwords online, which is why your passwords are easily accessible across devices. On the downside, copies of your passwords exist online that someone could possibly steal. On the positive side, Bitwarden encrypts and hashes all data before it leaves your device.
Technically, someone can circumvent Bitwarden’s security, or they can get their hands on your master password. With offline options like KeePass, someone needs access to your computer to get your passwords.
In contrast to proprietary alternatives, Bitwarden’s code is openly available for others to review and audit. This offers greater peace of mind that the company is securing your data to the extent promised and that it isn’t doing anything fishy with the information you provide.
You can create an account and sync all of your passwords for free. A paid option adds 1GB of file storage, support for additional authentication methods such as YubiKey and FIDO U2F, and more.
Download: Bitwarden (Free)
8. Your Browser

Mozilla Firefox comes preinstalled with most popular versions of Linux. Alternatives like Google Chrome and Vivaldi are only a download away. All three can save your passwords for you and automatically enter them when you visit a site. They can also sync your passwords between multiple computers.
You don’t need a major cross-platform browser to enjoy these features. Linux-only browsers such as GNOME Web and Falkon can save your passwords too. Basically any Linux web browser will do.
No matter which web browser’s password manager you use, understand that this isn’t the most secure option. If you share your computer with anyone, unless they’re signed into a different user account, autofill can give them easy access to your web accounts. Some browsers do a decent job encrypting your passwords and requiring a master password, while others make them available in plain text. And if you choose to sync your passwords, then copies of them may exist online.
What About LastPass on Linux?
LastPass supports Linux. As do other commercial, web-based services such as Dashlane and 1Password. If a password manager works in Chrome or Firefox, chances are you can run it on Linux.
There are also a few older projects that still exist in your Linux app store, but haven’t seen an update in years. Such apps include Revelation and Universal Password Manager. If you happen to like either one, maybe you could be the person to breathe in new life.
Still not sure you need a password manager? Here are some pseudo-superpowers password managers can give you.
Read the full article: The 8 Best Linux Password Managers to Stay Secure
Read Full Article
The Google Home Commands Cheat Sheet

Your Google Home is a hub of information, convenience, and fun. With just a few words, you can adjust your thermostat, play a game, or find out who starred in that movie. With so much information at your fingertips, it can be tough to remember everything your Google Home can do.
That’s why we’ve assembled this Google Home commands cheat sheet with nearly 100 useful commands. Most of these commands work with Google Assistant on Android as well, so you don’t even need a Google Home device to take advantage of them.
While we’ve outlined basic commands below, Google Home has a lot more to offer. Make sure you’ve read our beginner’s guide to Google Home before diving in.
You can ask connected questions and the Assistant will understand. For instance, after Google provides the answer to your question “Who sings the song Careless Whisper?”, you can say “Play that song.”
Additionally, if you’re in the US, you can ask your Google Home to do multiple actions at once. Just say “and” between two commands. For example, you might say “Hey Google, what time is it in Sydney and what’s the weather there?”
Before each of these commands, you’ll need to say “OK Google” or “Hey Google” to wake up your device. However, if you enable the Continued Conversations feature in the Home app, you can add a follow-up command without saying the wake phrase.
The Google Home Commands Cheat Sheet
| Command | Action |
|---|---|
| Google Home Device Control | |
| Help | Get help using Google Home |
| Turn it up / Louder | Raise the volume |
| Turn it down | Lower the volume |
| Set volume to [1-11] | Choose volume level |
| Mute | Prevent your speaker from listening. You'll have to press the physical button to unmute it. |
| Stop | Cancel the current action |
| Send feedback | Provide your thoughts about Google Home |
| Basic Google Home Functions | |
| Set alarm for [time] | Set a single alarm for the time you choose |
| Set alarm for [time] every day of the week | Set a recurring alarm |
| Cancel my alarm | Cancel your existing alarm |
| Snooze | Snooze a ringing alarm |
| Remind me to [task] on [day] at [time] | Set a reminder for a specific time |
| Set a timer for [X] minutes | Set a timer |
| Set a second timer for [X] minutes | Set a second timer |
| How much time is left on my timer? | Hear the remaining time on any timer |
| Pause timer | Pause a running timer |
| Resume timer | Resume a paused timer |
| Add [item] to my shopping list | Add an item to your Google Home shopping list |
| What's on my shopping list? | Hear the current contents of your shopping list |
| Buy [item] | Order from Google Express |
| Talk to [action name] | Interact with third-party Google Home skills |
| Food and Health Information | |
| How much potassium is in a banana? | Get information about food |
| How many calories are in [food]? | Get more nutritional information |
| What is [medical condition]? | Hear basic medical info |
| How do I make [dish]? | Get a recipe to make anything |
| Fine me a [food] recipe | Get a recipe for an ingredient you want to use up |
| Sports and Entertainment | |
| What was the score of the [team] game? | Hear the latest sports scores |
| What is the [team] record? | See how your favorite sports team is doing |
| When are the [team] playing next? | Check the next upcoming game |
| What actors are in [movie]? | Get entertainment-related news |
| Who invented [thing]? | Learn historical information |
| Who wrote [book]? | Find out who wrote books. who directed movies, and more |
| What is [actor]'s most popular movie? | Learn more about celebrities |
| Who is [person]? | Find out what Google knows about a person |
| How old is [person]? | Get information about famous figures |
| Calculations and Conversions | |
| How many days until [holiday]? | Count down to your favorite holidays |
| Count to [X] | Google will count out loud to your number |
| What's [X divided by [Y]? | Perform basic math |
| What is [X] percent of [Y]? | Perform more math calculations |
| What's the cosine of [X]? | Perform advanced math |
| How many [units] are in [other units] | Convert currency, units of measure, and more |
| How many pesos in a dollar? | Perform currency conversions |
| How many milligrams is [X] ounces? | Convert units |
| Language | |
| How do I spell [word]? | Hear a word spelled aloud |
| How do you say [word/phrase] in [language]? | Translate words and phrases |
| What is [foreign phrase] in English? | Translate any language to your own |
| What does [word] mean? | Get definitions for unknown words |
| Commute and Travel Details | |
| How's my commute? | Hear the estimated time to get to your work address |
| How's the traffic on the way to [location]? | Get traffic data for any destination |
| How long will it take to walk to [place]? | Find out how long it will take to reach a destination by any method |
| How far is [place] from here? | Find out about specific distance |
| When is my next flight? | Get the time for your next flight |
| Is my flight on time? | Check whether your flight is on time or delayed |
| What's the status of [airline] [flight number]? | Get details about any flight |
| How much is a flight to [place]? | Get flight quotes |
| What's the capital of [country]? | Hear geographical information |
| What time is it in [place]? | Hear the local time anywhere |
| Calendar and To-Do | |
| Play my daily briefing | Includes the time, weather, and news |
| What's on my calendar for [day]? | Get briefed on your first three events of the day |
| When is [holiday] this year? | Get a specific date |
| Remember [thing] | Store a quick note in Google Assistant's memory |
| What did I ask you to remember? | Recall earlier notes |
| What/when is my next event? | Hear info on your next scheduled Google Calendar meeting |
| News, Weather, and Local Info | |
| Tell me the news | Hear a digest of the latest news |
| What's the latest in [category]? | Get news about a topic such as sports or technology |
| What's the weather? | Hear the weather for your current location |
| What's the forecast for [day]? | Get a weather summary for a specific day |
| What is [stock] trading at? | Hear the current price of a given stock |
| How are the markets doing? | Get a summary of the latest stock market news |
| What [businesses] are nearby? | Find the closest restaurants, pharmacies, and more |
| What's the nearest [business]? | Find nearby restaurants, hotels, and more |
| What is the phone number for the nearest [place]? | Look up business phone numbers |
| Is [business] open now? | Get opening hours for a specific place |
| Google Home Music and Media Commands | |
| Play [song] | Play [album] | Play [artist] | Start playing music from your default service |
| Play [music] on [music service] | Play music from a service other than your default |
| Play music for [activity] | Play music based on a mood, genre, or activity |
| Play the song that goes [lyrics] | Play a song even if you don't know the title |
| Shuffle | Toggle shuffling of music |
| Pause | Pause your music |
| Resume | Continue playing paused music |
| Skip | Jump to the next song |
| Rewind [X] seconds | Back up in a podcast or news briefing |
| Stop in [X] minutes | Set a sleep timer |
| What's playing? | Hear info on the current song, podcast, etc. |
| Play [podcast name] | Start playing a chosen podcast |
| Listen to the latest episode of [podcast] | Hear the newest episode of any podcast |
| Play at [X] speed | Change podcast playback speed, such as 2x |
| Play [radio station] (on TuneIn) | Hear a radio station by call sign, frequency, or similar |
| Play my [station] station on Pandora | Play Pandora music (must link Pandora account in Google Home settings) |
| Play [audiobook] | Listen to an audiobook from Google Play Books |
| Google Home Chromecast Commands | |
| Turn on/off [Chromecast name] | Toggle the power of a connected Chromecast |
| Play [music] on [Chromecast name] | Start playing music on a connected Chromecast |
| Play on [Chromecast name] | Start playing a YouTube video on your Chromecast |
| Play [show or movie] on [TV name] | Play content from Netflix on your TV |
| Play/pause [Chromecast name] | Halt or resume Chromecast playback |
| Stop [Chromecast name] | End Chromecast media playback |
| Skip forward/back [X] minutes on [Chromecast name] | Rewind or fast-forward what your Chromecast is playing |
| Mute/unmute [Chromecast name] | Silence or resume Chromecast audio |
| Show [camera name] | Show your smart camera's feed on your Chromecast |
| Show photos on my TV | Use your Chromecast to show your Google Photos |
| Show me a picture of [thing] | See a picture on your Chromecast display |
| Google Home Smart Home Commands | |
| Turn on/off my lights | Toggle smart lights |
| Set my lights to [X] percent | Dim/brighten smart lights |
| Turn my lights [color] | Change the color of your smart bulbs |
| What's the temperature inside? | Find out about the indoors temperature |
| Set the temperature to [X] | Control the climate via your Nest thermostat |
| Lock the front door | Lock your smart locks |
| Broadcast [message] | Send a message all other Google Home speakers in your home |
| Google Home Phone Commands | |
| Read my replies | Hear the latest messages from Messenger, WhatsApp, SMS, and more |
| Send a WhatsApp message | Message via voice in WhatsApp (must link your account in the Home app) |
| Call [contact] | Place a call through your Google Home |
| Hang up | End the current call |
| Find my phone | Ring your phone to help locate it |
| Bluetooth pairing | Pair with Bluetooth |
| Fun Google Home Commands | |
| Play Lucky Trivia | Play a trivia game to challenge your knowledge |
| What are your Easter eggs? | Hear some of Google Home's funny responses |
| What does [animal] sound like? | Make Google imitate sounds |
| Sing a song | Hear Google Assistant's hit new single |
| Tell me a story | Listen to Google Asisstant recite a tale |
| Tell me a joke | Google Assistant will make you laugh |
| Read a poem | Hear Google Home wax eloquent with some poetry |
| Repeat after me: [phrase] | Google Home will repeat whatever you say |
| Give me a random number between [X] and [Y] | Get a randomly generated number |
| Roll a die | Have Google Home roll a virtual die |
| Flip a coin | Google Home will flip a virtual coin |
| What is your quest? | Find out Google Assistant's driving force in life |
| Can you swim? | Ask Google Assistant about herself |
| Talk to Eliza | Speak with a virtual therapist, who really isn't much help |
| Up up, down down, left right, left right, B A, Start | Get 30 extra lives |
| Beatbox | Hear Google Home break it down |
| Mad Libs | Play the classic word game with Google Assistant |
| Play the name game | Google Assistant will come up with a rhyme for any name |
| Make me a sandwich | See what she says! |
| Where's Waldo? | Because Google Assistant knows everything |
| Surprise me | Are you feeling lucky? |
| Miscellaneous Google Home Commands | |
| Tune my instrument | Hear notes to help get your instrument in tune |
| Play a [letter] note | Hear a musical note |
| Where's my package? | Hear the status of your shipped order |
There’s More to Master With Google Home
Now, you have dozens of commands to try on your Google Home device. Hopefully they will help you make the most of your device and remember its most useful tricks. And if this isn’t enough, we’ve previously looked at some entertaining Google Home commands .
If you find yourself repeating the same commands every day, there’s another Google Assistant feature you should know about. It’s called Routines, and it allows you to create sets of actions that fire when you give a certain command or a specific time of the day passes. Check out our guide to Google Assistant routines to get started.
Read the full article: The Google Home Commands Cheat Sheet
Read Full Article
What Is Code-Signed Malware and How Do You Avoid It?

Code signing is the practice of cryptographically signing a piece of software so that the operating system and its users can verify that it is safe. Code signing works well, by and large. The majority of the time, only the correct software uses its corresponding cryptographic signature.
Users can download and install safely, and developers protect the reputation of their product. However, hackers and malware distributors are using that exact system to help malicious code slip past antivirus suites and other security programs.
How does code-signed malware and ransomware work?
What Is Code Signed Malware?
When software is code-signed, it means that the software carries an official cryptographic signature. A Certificate Authority (CA) issues the software with a certificate confirming that the software is legitimate and safe to use.
Better still, your operating system takes care of the certificates, code checking, and verification, so you don’t have to worry. For instance, Windows uses what is known as a certificate chain. The certificate chain consists of all the certificates needed to ensure the software is legitimate at every step of the way.
“A certificate chain consists of all the certificates needed to certify the subject identified by the end certificate. In practice, this includes the end certificate, the certificates of intermediate CAs, and the certificate of a root CA trusted by all parties in the chain. Every intermediate CA in the chain holds a certificate issued by the CA one level above it in the trust hierarchy. The root CA issues a certificate for itself.”
When the system works, you can trust software. The CA and code signing system require a huge amount of trust. By extension, malware is malicious, untrustworthy, and should not have access to a Certificate Authority or code signing. Thankfully, in practice, that is how the system works.
Until malware developers and hackers find a way around it, of course.
Hackers Steal Certificates From Certificate Authorities
Your antivirus knows that malware is malicious because it has a negative effect on your system. It triggers warnings, users report problems, and the antivirus can create a malware signature to protect other computers using the same antivirus tool.
However, if the malware developers can sign their malicious code using an official cryptographic signature, none of that will happen. Instead, the code-signed malware will walk through the front door as your antivirus and the operating system rolls out the red carpet.
Trend Micro research found that there is an entire malware market supporting the development and distribution of code-signed malware. Malware operators gain access to valid certificates which they use to sign malicious code. The following table shows the volume of malware using code signing to evade antivirus, as of April 2018.

The Trend Micro research found that around 66 percent of the malware sampled was code-signed. Furthermore, certain malware types come with more code signing instances, such as Trojans, droppers, and ransomware. (Here are seven ways to avoid a ransomware attack!)
Where Do Code Signing Certificates Come From?
Malware distributors and developers have two options regarding officially signed code. Certificates are either stolen from a Certificate Authority (directly, or for resale), or a hacker can attempt to mimic a legitimate organization and fake their requirements.
As you would expect, a Certificate Authority is a tantalizing target for any hacker.
It isn’t just hackers fueling the rise in code-signed malware. Allegedly unscrupulous vendors with access to legitimate certificates sell trusted code-signing certificates to malware developers and distributors, too. A team of security researchers from Masaryk University in the Czech Republic and Maryland Cybersecurity Center (MCC) discovered four organizations selling [PDF] Microsoft Authenticode certificates to anonymous buyers.
“Recent measurements of the Windows code signing certificate ecosystem have highlighted various forms of abuse that allow malware authors to produce malicious code carrying valid digital signatures.”
Once a malware developer has a Microsoft Authenticode certificate, they can sign any malware in an attempt to negate Windows security code-signing and certificate-based defense.
In other cases, rather than steal the certificates, a hacker will compromise a software build server. When a new software version releases to the public, it carries a legitimate certificate. But a hacker can also include their malicious code in the process. You can read about a recent example of this type of attack below.
3 Examples of Code-Signed Malware
So, what does code-signed malware look like? Here are three code-signed malware examples:
- Stuxnet malware. The malware responsible for destroying the Iranian nuclear program used two stolen certificates to propagate, along with four different zero-day exploits. The certificates were stolen from two separate companies—JMicron and Realtek—that shared a single building. Stuxnet used the stolen certificates to avoid the then newly-introduced Windows requirement that all drivers required verification (driver signing).
- Asus server breach. Sometime between June and November 2018, hackers breached an Asus server the company uses to push software updates to users. Researchers at Kaspersky Lab found that around 500,000 Windows machines received the malicious update before anyone realized. Instead of stealing the certificates, the hackers signed their malware with legitimate Asus digital certificates before the software server distributed the system update. Luckily, the malware was highly targeted, hard-coded to search for 600 specific machines.
- Flame malware. The Flame modular malware variant targets Middle Eastern countries, using fraudulently signed certificates to avoid detection. (What is modular malware, anyway?) The Flame developers exploited a weak cryptographic algorithm to falsely sign the code signing certificates, making it appear as if Microsoft had signed them off. Unlike Stuxnet which carried a destructive element, Flame is a tool for espionage, seeking out PDFs, AutoCAD files, text files, and other important industrial document types.
How to Avoid Code-Signed Malware
Three different malware variants, three different types of code signing attack. The good news is that most malware of this type is, at least at the current time, highly targeted.
The flipside is that because of the success rate of such malware variants that use code signing to avoid detection, expect more malware developers to use the technique to make sure their own attacks are successful.
As well as this, protecting against code-signed malware is extremely difficult. Keeping your system and antivirus suite up to date is essential, avoid clicking on unknown links, and double-check where any link is taking you before following it.
Other than updating your antivirus, check our list of how you can avoid malware!
Read the full article: What Is Code-Signed Malware and How Do You Avoid It?
Read Full Article
5 Functional Programming Languages You Should Know

If you spend any amount of time reading up on programming trends on the internet, you’ll have heard about functional programming. The term is thrown about fairly often, but what does it mean?
Even if you’re aware of what functional programming is, you may be unclear about which languages are best suited for it. After all, not all programming languages are created equal. While you can apply functional programming paradigms in many languages, there are still some where you’ll feel much more comfortable.
What Is Functional Programming?
If you have a background in mathematics, you have a head start on functional programming. This is because the functional programming paradigm treats computing like mathematical functions. If you don’t have a mathematical background, this could leave you feeling confused.
Basically, functional programming treats functions and data as immutable. You pass data into a function, and it generally returns that data transformed or some other type of data. In functional programming, the function should never change the original data or program state.
There is a similarity to the Unix philosophy that each program should do one thing well. A function shouldn’t touch various parts of your program. Instead, it should take its input and give you an output.
Ideally, functions should be pure whenever possible in functional programming. This means that given the same input, the function’s output will always remain the same.
Functional vs. Object-Oriented Programming
This is a dramatic departure from something like object-oriented programming. In object-oriented programming, you often have a base object with various methods dedicated to changing either data or state that are part of that object. A method may even alter data or state if not explicitly stated.
In practical programs, sometimes this makes sense. That said, it can make programs harder to maintain, as it’s not always clear what is altering state or data. Functional programming was originally used in academic environments, but can also help to prevent these sorts of problems.
1. JavaScript

Some programming languages allow functional programming while others either encourage or even enforce it. JavaScript falls in the first category. While you can use functional programming paradigms in the language, you can just as easily use an object-oriented approach.
That said, there are plenty of functional programming paradigms built into JavaScript. Take, for example, higher-order functions. These are functions that can take other functions as arguments.
JavaScript has several functions that work with arrays like map(), reduce(), filter(), and others, all of which are higher-order functions. This lets you chain them together to quickly do all manner of things with an array.
While early JavaScript had some issues with mutability, newer versions of the ECMAScript standard provide fixes. Instead of the catch-all var keyword for defining variables, you now have const and let. The first lets you define constants, as the name implies. The second, let, limits the scope of a variable to the function in which it is declared.
2. Python

Like JavaScript, Python is a generalized language that you can use any number of programming paradigms with. Python may have its downsides, but functional programming isn’t one of them. There is even an introduction to functional programming in the official Python documentation.
To start, you’ll find many of the same map(), filter(), reduce(), and similar functions mentioned above built-in. As with JavaScript, these are higher-order functions as they take other functions as arguments. In Python, functional programming has an advantage in the form of the lambda keyword.
You can use lambda expressions in a few ways. One way to use it is as shorthand for simple functions. When assigned to a variable, you can call lambda expressions exactly as you would a standard Python function. The real advantage of lambda expressions comes when you use them as anonymous functions.
Anonymous functions work in JavaScript and other languages on this list as well. They come in especially handy when used with higher-order functions since you can define them on the spot. Without anonymous functions, you’d have to pre-define even simple additions as bespoke functions.
3. Clojure

Unlike JavaScript and Python, Clojure may not exactly be a household name, even among programmers. In case you’re not familiar, Clojure is a dialect of the Lisp programming language, which dates back to the late 1950s. This brings along with it a very specific way of doing things that happens to be perfect for functional programming.
Like other Lisp dialects, Clojure treats code as data. This means that the code can effectively alter itself. Unlike other Lisp dialects, Clojure runs on the Java platform and is compiled to JVM bytecode. This means it can work with Java libraries, whether they were written in Clojure or not.
Unlike previous languages on this list, Clojure is a functional programming language from the ground up. That means that it advocates immutability wherever possible, especially within data structures.
Clojure doesn’t expect all programs to be mathematically “provable,” but encourages using pure functions wherever possible.
4. Elm

One of the newer languages on this list, Elm is a purely functional language initially designed by Evan Czaplicki in 2012. The language has gained popularity among web developers, specifically for creating user interfaces.
Unlike every prior entry on this list, Elm uses static type checking. This helps to ensure no runtime exceptions, with errors instead caught at compile time. This means less visible errors for users, which is a major plus.
The Elm compiler targets HTML, CSS, and JavaScript. In the same way that you can use Clojure to write programs that run on Java, you can write apps that use JavaScript libraries in Elm.
One major difference between Elm and other languages here is that you won’t find generic filter(), map(), and similar functions. Instead, these are defined by data type like List.map or Dict.map.
5. Haskell

Haskell is another statically typed, purely functional language. Unlike Elm, Haskell has been around for a while. The first version of the language was designed in 1990. The latest standard is Haskell 2010, while the next version is planned for 2020.
As we’ve already explored, Haskell’s purely functional nature means that by design, functions shouldn’t have side effects. This makes it well-suited to solving real-world problems despite functional programming’s roots in academia.
Despite its lack of mainstream popularity, Haskell has been employed in some widely used projects. The Xmonad window manager is written entirely in Haskell. Pandoc, which converts different types of markup to and from other formats also uses the language.
The standard map(), filter(), reduce(), and other higher-order functions are present, which should let you take concepts from JavaScript or Python to Haskell. If you want to learn more about the language, Learn You a Haskell for Great Good is a popular starting point.
Are You New to Programming?
Some of the above terms and languages may seem somewhat esoteric if you’re not yet a seasoned coder. That’s good, as knowing what you don’t know is one of the first steps in becoming a better learner.
Some of the languages listed above are better for beginners than others. Take a look at our list of the best programming languages for beginners. You’ll notice there is some crossover between the two lists.
Read the full article: 5 Functional Programming Languages You Should Know
Read Full Article
You Can Now Play Minecraft for Free in Your Browser

Minecraft is 10 years old, and to celebrate this milestone, Mojang has released Minecraft Classic for the web. This means you can play Minecraft in your web browser. You don’t need to download anything, and Minecraft Classic is completely free to play.
How to Play Minecraft for Free in Your Browser
Minecraft Classic has been available to play for free for many years. And this isn’t the first time it has been available to play in your web browser. However, Minecraft Classic was previously only available on Windows, Mac, and Linux, and required Java.
Now, you just need to point your browser at the Minecraft Classic website and you can play for free without the need to download anything. The only requirement seems to be a keyboard, so you can’t play on your smartphone or tablet. Sadly.
You know what’s better than new content? Good ol’ nostalgia! To celebrate the 10 year anniversary of Minecraft, we’re releasing MINECRAFT CLASSIC to your browser. Play the original creative mode, complete with 32 blocks and all the beloved bugs!
? https://t.co/7pGSj3omzR ? pic.twitter.com/gTZcls7tBe
— Minecraft (@Minecraft) May 7, 2019
As the name suggests, Minecraft Classic isn’t the Minecraft of 2019. Instead, it’s the game as it existed in 2009. This means you’ll have to put up with a clunky user interface, be stuck with just 32 blocks to build with, and more bugs than the average rainforest.
Minecraft Classic only allows you to play in Creative mode, so there’s no Survival mode with enemies to fight off. There’s also no way to save your game. Still, you can invite up to nine friends to join your game just by sending them the link.
Minecraft Classic Is a Piece of Gaming History
Let’s not kid ourselves here; Minecraft Classic cannot compete with the current version of the game. Still, it’s free, and can be played in your web browser with no effort on your part. So you may as well take the opportunity to sample a piece of gaming history.
We covered Minecraft a lot in its early days, so if you’re new to the game you should check out our beginner’s guide to Minecraft (for latecomers). If, on the other hand, you’re a veteran you may be interested in learning how to create your own Minecraft mod.
Read the full article: You Can Now Play Minecraft for Free in Your Browser
Read Full Article
Smartphone shipments hit a five year low in North America
More dismal news from the smartphone number crunchers. New figures out of Canalys put the North American smartphone market at five year low for the first quarter of 2019. That’s…bad. But also, pretty inline with what we’ve been seeing globally. The market has stagnated, and while manufacturers aren’t in full on panic mode, there’s certainly cause for concern.
Shipments dropped from 44.4 million down to 36.4 million, marking an an 18 percent drop year over year for the first quarter. Canalys says it’s the steepest drop it’s recorded for the category, chalking some of the issues up to “a lackluster performance by Apple and the absence of ZTE.”
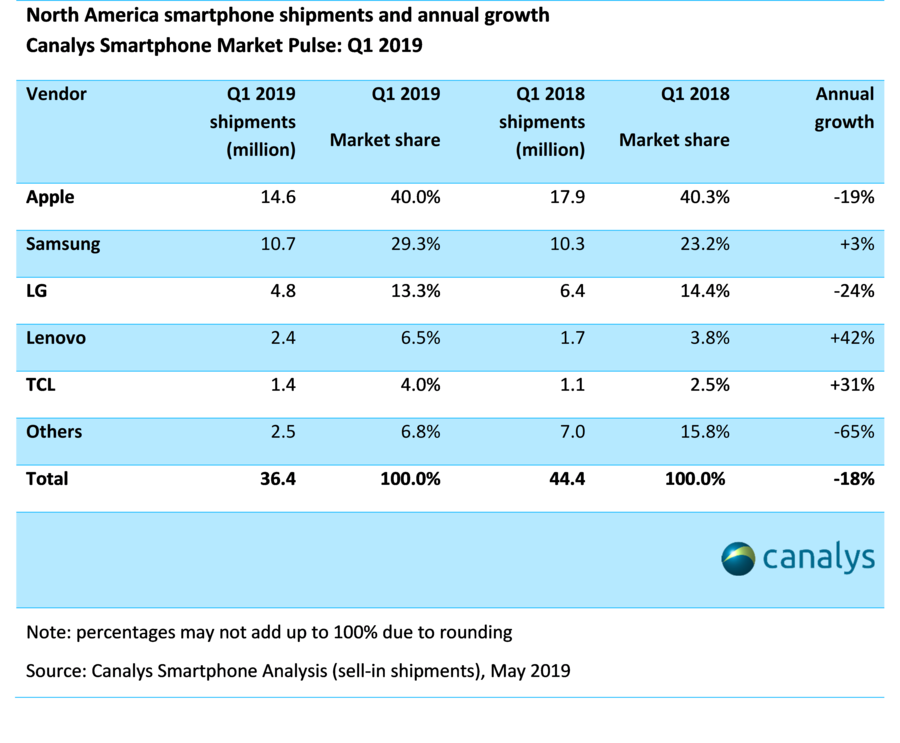
Apple is still the top of the heap, commanding 40 percent of the North American market with help from the sale of older discounted units. But Samsung managed to to tighten the gap on the back of a successful Galaxy S10 launch. The company grew by three percent for the year, up to 29.3 percent of the market.
LG, Lenovo and TCL rounded out the top five, with the latter two making pretty solid marketshare strides. The remainder of the market took a massive hit, however, with a 65 percent drop off in shipments. Analysts seem confident that 5G imminent arrival will help give the market a boost in coming quarters, but it’s going to be hard for manufacturers to maintain that momentum.
Read Full Article