
Router, network device, and Internet of Things malware is increasingly common. Most focus on infecting vulnerable devices and adding them to powerful botnets. Routers and Internet of Things (IoT) devices are always powered-up, always online, and waiting for instructions. Perfect botnet fodder, then.
But not all malware is the same.
VPNFilter is a destructive malware threat to routers, IoT devices, and even some network-attached storage (NAS) devices. How do you check for a VPNFilter malware infection? And how can you clean it up? Let’s take a closer look at VPNFilter.
What Is VPNFilter?
VPNFilter is a sophisticated modular malware variant that primarily targets networking devices from a wide range of manufacturers, as well as NAS devices. VPNFilter was initially found on Linksys, MikroTik, NETGEAR and TP-Link network devices, as well as QNAP NAS devices, with around 500,000 infections in 54 countries.
The team that uncovered VPNFilter, Cisco Talos, recently updated details regarding the malware, indicating that networking equipment from manufacturers such as ASUS, D-Link, Huawei, Ubiquiti, UPVEL, and ZTE are now showing VPNFilter infections. However, at the time of writing, no Cisco network devices are affected.
The malware is unlike most other IoT-focused malware because it persists after a system reboot, making it difficult to eradicate. Devices using their default login credentials or with known zero-day vulnerabilities that have not received firmware updates are particularly vulnerable.
What Does VPNFilter Do?
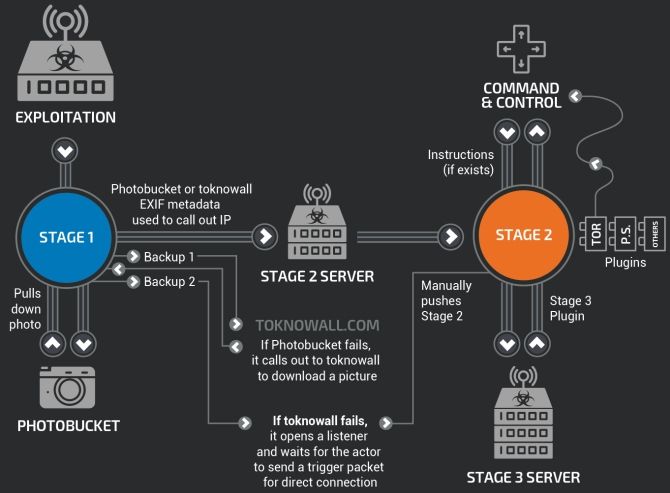
So, VPNFilter is a “multi-stage, modular platform” that can cause destructive damage to devices. Furthermore, it can also serve as a data collection threat. VPNFilter works in several stages.
Stage 1: VPNFilter Stage 1 establishes a beachhead on the device, contacting its command and control server (C&C) to download additional modules and await instructions. Stage 1 also has multiple inbuilt redundancies to locate Stage 2 C&Cs in case of infrastructure change during deployment. The Stage 1 VPNFilter malware is also able to survive a reboot, making it a robust threat.
Stage 2: VPNFilter Stage 2 does not persist through a reboot, but it does come with a wider-range of capabilities. Stage 2 can collect private data, execute commands, and interfere with device management. Also, there are different versions of Stage 2 in the wild. Some versions are equipped with a destructive module that overwrites a partition of the device firmware, then reboots to render the device unusable (the malware bricks the router, IoT, or NAS device, basically).
Stage 3: VPNFilter Stage 3 modules work like plugins for Stage 2, extending the functionality of VPNFilter. One module acts as a packet sniffer that collects incoming traffic on the device and steals credentials. Another allows the Stage 2 malware to communicate securely using Tor. Cisco Talos also found one module that injects malicious content into traffic passing through the device, meaning the hacker can deliver further exploits to other connected devices through a router, IoT, or NAS device.
In addition, VPNFilter modules “allow for the theft of website credentials and the monitoring of Modbus SCADA protocols.”
Photo Sharing Meta
Another interesting (but not newly discovered) feature of the VPNFilter malware is its use of online photo sharing services to find the IP address of its C&C server. The Talos analysis found that the malware points to a series of Photobucket URLs. The malware downloads the first image in the gallery the URL references and extracts a server IP address hidden within the image metadata.
The IP address “is extracted from six integer values for GPS latitude and longitude in the EXIF information.” If that fails, the Stage 1 malware falls back to a regular domain (toknowall.com—more on this below) to download the image and attempt the same process.
Targeted Packet Sniffing
The updated Talos report revealed some interesting insights into the VPNFilter packet sniffing module. Rather than just hoovering everything up, it has a fairly strict set of rules that target specific types of traffic. Specifically, traffic from industrial control systems (SCADA) that connect using TP-Link R600 VPNs, connections to a list of pre-defined IP addresses (indicating an advanced knowledge of other networks and desirable traffic), as well as data packets of 150 bytes or larger.
Craig William, senior technology leader, and global outreach manager at Talos, told Ars, “They’re looking for very specific things. They’re not trying to gather as much traffic as they can. They’re after certain very small things like credentials and passwords. We don’t have a lot of intel on that other than it seems incredibly targeted and incredibly sophisticated. We’re still trying to figure out who they were using that on.”
Where Did VPNFilter Come From?
VPNFilter is thought to be the work of a state-sponsored hacking group. That the initial VPNFilter infection surge was predominantly felt throughout Ukraine, initial fingers pointed to Russian-backed fingerprints and the hacking group, Fancy Bear.
However, such is the sophistication of the malware there is no clear genesis and no hacking group, nation-state or otherwise, has stepped forward to claim the malware. Given the detailed malware rules and targeting of SCADA and other industrial system protocols, a nation-state actor does seem most likely.
Regardless of what I think, the FBI believes VPNFilter is a Fancy Bear creation. In May 2018, the FBI seized a domain—ToKnowAll.com—that was thought to have been used to install and command Stage 2 and Stage 3 VPNFilter malware. The domain seizure certainly helped stop the immediate spread of VPNFilter, but didn’t sever the main artery; the Ukrainian SBU took-down a VPNFilter attack on a chemical processing plant in July 2018, for one.
VPNFilter also bears similarities to the BlackEnergy malware, an APT Trojan in use against a wide-range of Ukrainian targets. Again, while this is far from complete evidence, the systemic targeting of Ukraine predominantly stems from hacking groups with Russian ties.
Am I Infected With VPNFilter?
Chances are, your router is not harboring the VPNFilter malware. But it is always better to be safe than sorry:
- Check this list for your router. If you’re not on the list, everything is okay.
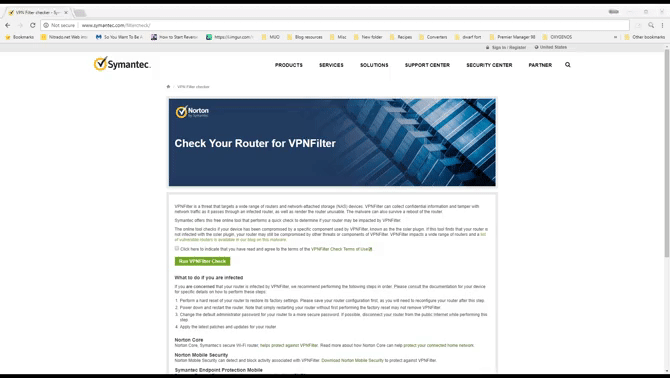
- You can head to the Symantec VPNFilter Check site. Check the terms and conditions box, then hit the Run VPNFilter Check button in the middle. The test completes within seconds.
I’m Infected With VPNFilter: What Do I Do?
If the Symantec VPNFilter Check confirms that your router is infected, you have a clear course of action.
- Reset your router, then run the VPNFilter Check again.
- Reset your router to factory settings.
- Download the latest firmware for your router, and complete a clean firmware installation, preferably without the router making an online connection during the process.
Further to this, you need to complete full system scans on each device connected to the infected router.
You should always change the default login credentials of your router, as well as any IoT or NAS devices (IoT devices don’t make this task easy) if at all possible. Also, while there is evidence that VPNFilter can evade some firewalls, having one installed and properly configured will help keep a lot of other nasty stuff out of your network.
Watch Out for Router Malware!
Router malware is increasingly common. IoT malware and vulnerabilities are everywhere, and with the number of devices coming online, will only get worse. Your router is the focal point for data in your home. Yet it doesn’t receive nearly as much security attention as other devices.
Simply put, your router isn’t secure as you think.
Read the full article: How to Spot VPNFilter Malware Before It Destroys Your Router
Read Full Article
No comments:
Post a Comment