Google is famous for a lot of things, but privacy and security aren’t usually on the top of that list. Alongside Facebook, they are often heavily criticized for their behavior with your data. Whether it’s scanning your Gmail inbox to show you targeted ads or cooperating with the NSA to spy on users around the world, there’s a lot to be critical of.
At first glance, it would seem like you shouldn’t trust Google at all. But looks can be deceiving. Behind the countless headlines on privacy concerns, Google is working hard to improve your security.
1. Capture The Flag
Bug bounty programs are common in the tech world. Software companies promise rewards to programmers, hackers, and security experts who find vulnerabilities in their products. The company harnesses the power of a worldwide network of experts, who get to hone their skills and earn money at the same time. Capture The Flag (CTF) events also take advantage of the skill of experts, but use gamification and teamwork to get the job done.
CTF events differ from bug bounty programs though. To be rewarded for on a bounty program, developers have to spend time hunting through the software’s code looking for potential problems. CTF sets challenges around known issues as part of a timed competition, with points awarded to the winning team. The organizers can set challenges around any topic, but the most popular focus is on reverse engineering, exploitation, and real-world attacks like ransomware.
Google hosted their first CTF in April 2016, and it is now an annual event. Teams sign up to the qualifying round, typically hosted a few weeks before the main contest. Four members from each of the top ten teams then get flown to one of Google’s offices to participate. Prizes are paid out to the top three teams, with the first place winners receiving $13,337.
All competing teams can submit challenge write-ups and could earn between $100 and $500 for their efforts. For the 2018 contest, Google introduced Beginners’ Quests for any first timers or those new to security. Although these quests don’t qualify for contest points, they are an enjoyable introduction to security research.
2. Safe Browsing
In May 2007, a year before Google launched their Chrome web browser, the search engine debuted its Safe Browsing anti-malware effort. They’d recognized that malware is commonly spread through “drive-by downloads” from compromised web servers. Google couldn’t patch the vulnerabilities in your web browser and plugins, but they decided they could alert you to potentially compromised websites in your search results.
Safe Browsing now protects over three billion devices worldwide. It’s not just Google products either—Safe Browsing is integrated into Firefox and Safari too. Even apps like Snapchat have begun to use Google’s Safe Browsing API to keep their users safe. As we live in an increasingly mobile world, Google has set an Unwanted Software Policy for Android. Any apps found to be in breach of that policy display warnings about misuse of data through Safe Browsing too.
3. HTTPS Everywhere
Your connection to a website isn’t secure; at least it didn’t use to be. If the URL of a site begins HTTP, then the connection isn’t encrypted. This means that any data sent between your device and the website’s server could be intercepted. These are known as man-in-the-middle attacks and allow an attacker to insert themselves between both devices and read all the data. Sites that handle sensitive data, like email and online banking providers, have used HTTPS encryption for many years to secure your data in transit.
Google decided that Chrome should do more to warn you when your connection isn’t encrypted. This helps you decide whether to enter payment details and to identify phishing websites. The padlock next to the URL bar is a simple and clear visual aid to keep you informed. Although this was progress, Google decided this still wasn’t enough.
Chrome is the world’s most popular web browser with a 60.6% usage share. Decisions and features implemented in Chrome have a significant impact across the internet. So when Google decided to advocate for the adoption of HTTPS it had a huge knock-on effect. They began moving non-HTTPS websites lower down search rankings, and displaying a “not secure” warning alongside Chrome’s padlock. It was initially placed only on HTTP sites that asked for your data, but in July 2018, Google enabled the “not secure” warning for all non-HTTPS sites.
4. Google Play Protect
To stem the flow of Android malware, Google introduced Google Play Protect at their developer conference I/O 2017. Android had security protections, but they often didn’t communicate with one another, gave vague advice, and required a fair amount of input from you. Play Protect unites a lot of these features under one name. It now protects over two billion devices and scans 50 billion apps every day.
Play Protect uses machine learning to help identify Potentially Harmful Apps (PHA). By training the system to recognize patterns of behavior similar to known PHAs, it can scan new apps and identify any that may be PHAs. According to Google, the behaviors include “apps that attempt to interact with other apps on the device, access or share your personal data, download something without your knowledge, connect to phishing websites, or bypass built-in security features.” Google’s security team reviews potential PHAs for confirmation. That information is fed back into the machine learning algorithms to improve its detection capabilities.
5. Accounts Settings & Security Checkup
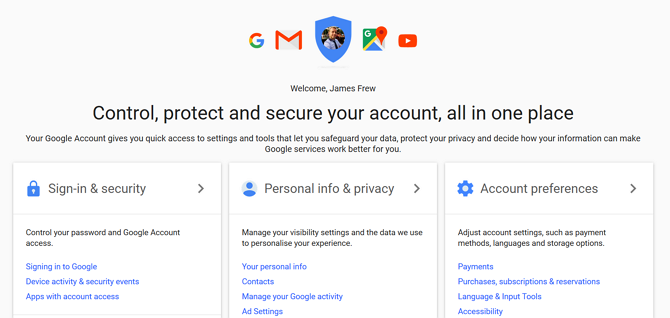
Hopefully, this won’t come as a surprise, but Google knows a lot about you; probably more than you realized. Unlike some of their contemporaries, though, they understand the importance of trust. You’d only feel comfortable with Google handling your location, emails, calendar, search history, YouTube uploads, and more, if you could be sure that data stays safely locked away inside your account.
As it contains so much personal information, the security of your Google account is critical, not just to you, but to Google too. The My Account dashboard has been designed to make securing your account and managing the data Google holds about you easy to maintain. The sidebar navigation lets you quickly switch between Sign-In & Security, Personal Info & Privacy, and Account Preferences.
Their Security check-up tool even guides you through the most crucial security settings so that if you don’t want to deep dive into all the settings, you don’t have to. When using Google products, you’ll occasionally be prompted to review your security settings. In the past, Google has even given away free Google Drive storage as a reward for completing the checkup.
Unlike Facebook, where a labyrinth of complex options get in your way, Google makes it very easy to view and remove data stored in your account. Navigate to the My Activity page, and you’ll be able to find your full history, filterable by product and date. Either select the data you want to delete or use the “Delete activity by” tool to easily find the information you want to be removed.
Do You Trust Google?
In many ways, Google deserves its reputation as a security and privacy nightmare. Their longstanding motto “don’t be evil” was even recently removed from the preface of their code of conduct. This was right around the time they courted controversy with their involvement in developing AI for military drones.
Despite these apparent concerns, Google is a large, complex company with many aims. Their commitment to security—even if it comes at the detriment to your privacy—is commendable. By using their considerable influence to remove malware from Android, and nurture the development of security professionals around the world, Google makes the internet safer for us all.
Read the full article: 5 Surprising Ways Google Improves Your Online Security
Read Full Article
No comments:
Post a Comment