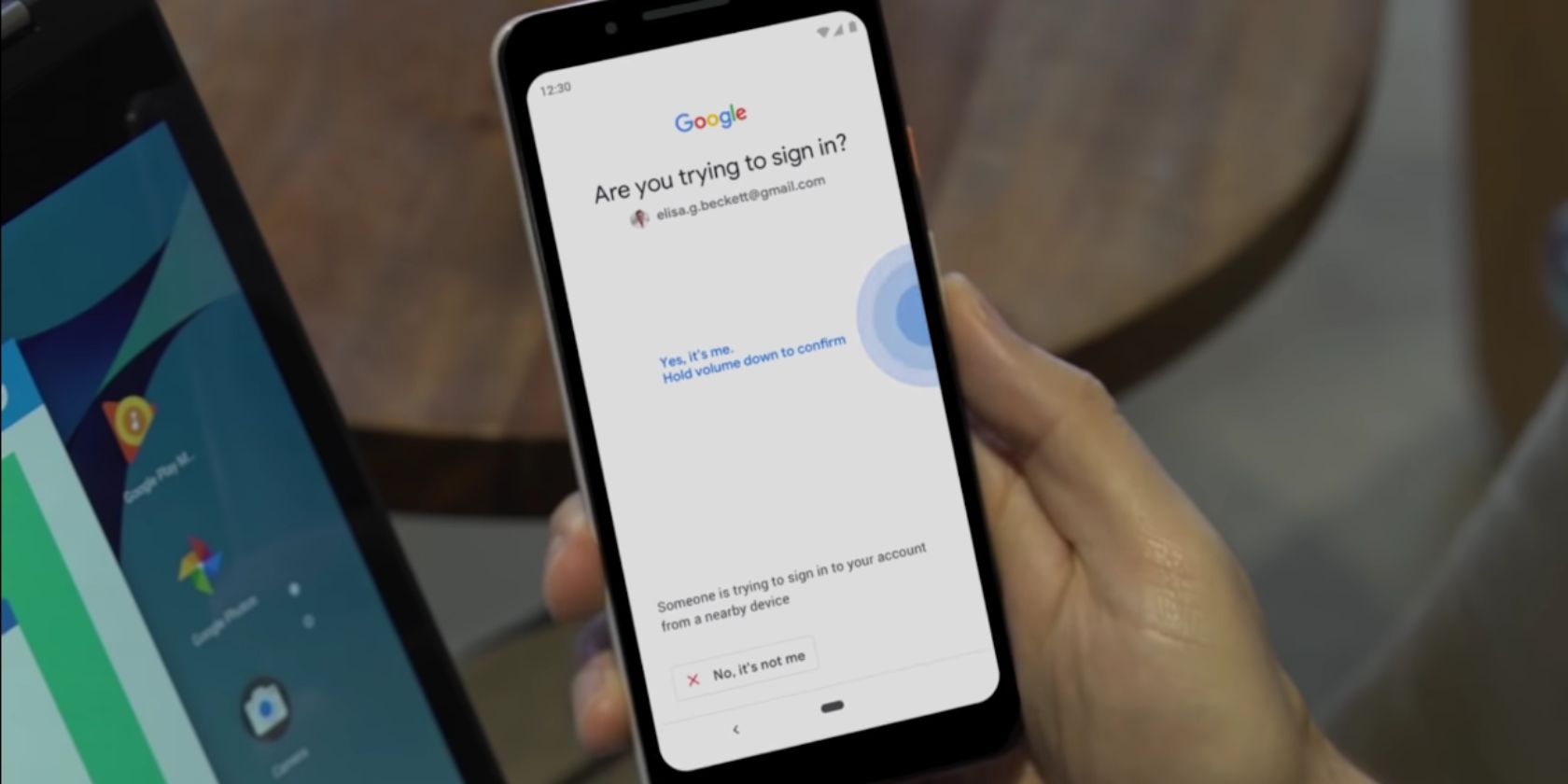
If you’re looking to protect your Google account from hackers, Google has a new 2FA trick up its sleeve. It involves using your Android handset as a security key, and it’s available to anyone who owns a device running Android 7.0 or later.
What Is Two-Factor Authentication?
Two-factor authentication or two-step verification is a key weapon in a fight against phishing. As the name suggests, 2FA or 2SV adds an extra element to the login procedure. This makes it much harder, though not impossible, for hackers to sign into your accounts.
2FA usually involves being sent an SMS text message or employing an authentication app. However, you can also use physical security keys such as dongles. Google’s latest innovation means you can now use your Android handset as a physical security key.
How to Use Your Phone as a Security Key
To use your phone as a security key all you need is handset running Android 7.0 or later, and a Bluetooth-enabled computer running Windows 10, macOS X, or Chrome OS. You must also be enrolled in Google two-step verification program.
Then, all you need to do is:
- Add your Google account to your Android phone.
- Sign into your account and turn on Bluetooth.
- Open Chrome on your computer and visit the Google Security page.
- Tap 2-Step Verification and click “Add Security Key”.
- Choose your phone from the list of available devices.
If you’re using a Google Pixel 3 you’ll be able to activate the security key by pressing the volume-down button. All other eligible Android devices will need to sign in and tap a button. This currently only works for logging into Google services.
For more detailed instructions, see this Google Support Note.
Fighting Back Against the Best Hackers
This may seem overkill for personal accounts, but with the best hackers using sophisticated methods to bypass security efforts, it’s worth doing. It’s also surprisingly simple to set up, so if you have a phone running Android 7.0+ it’s worth considering.
Read the full article: You Can Now Use Your Phone as a Security Key
Read Full Article
No comments:
Post a Comment