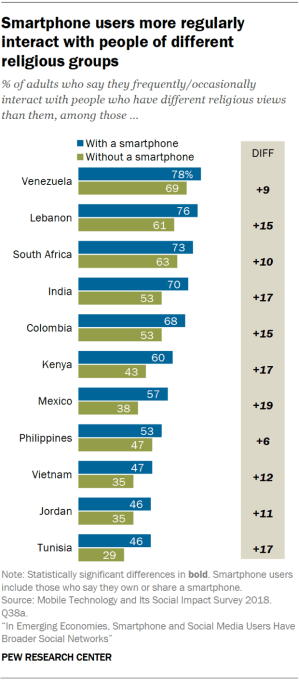
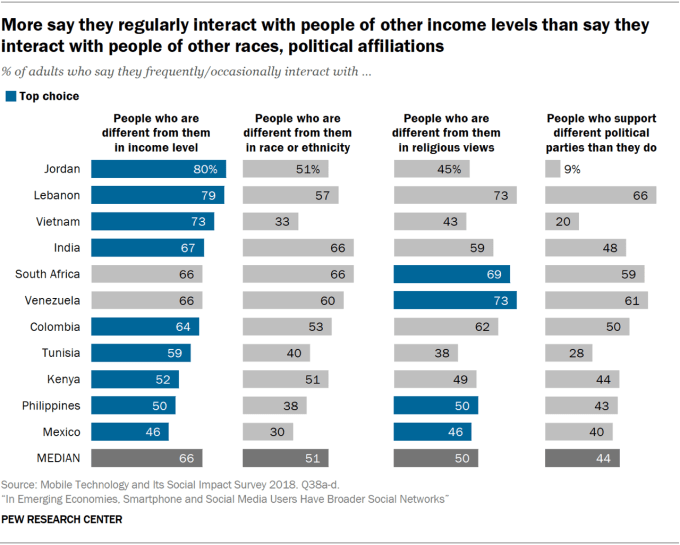
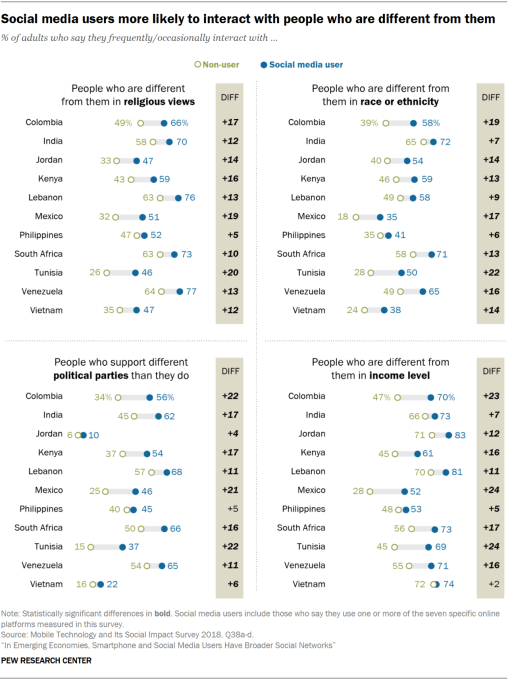
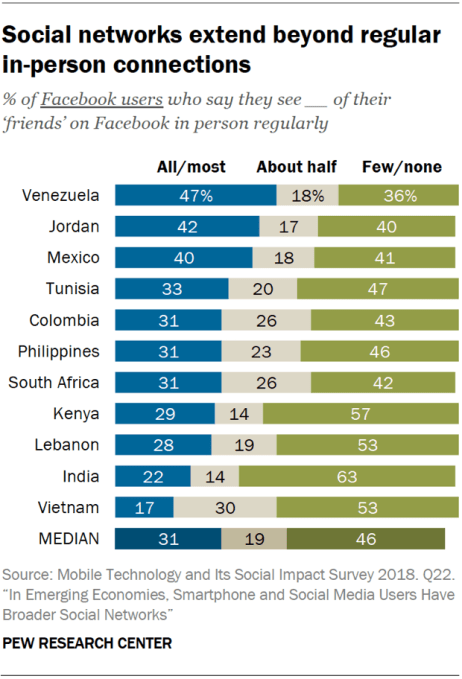
TechCrunch has learned of a safety issue and a number of product reliability questions being raised about a modular computer made by a London edtech startup that’s intended for children to learn coding and electronics.
The product, called the pi-top 3, is a Raspberry Pi-powered laptop with a keyboard that slides out to access a rail for breadboarding electronics.
A student at a US school had to be attended by a nurse after touching a component in the device which had overheated, leaving them with redness to their finger.
A spokesperson for Cornell Tech confirmed the incident to us — which they said had happened in June. We’ve withheld the name of the school at their request.
In an internal pi-top email regarding this incident, which we’ve also reviewed, it describes the student being left with “a very nasty finger burn”.
Cornell Tech’s spokesperson told us it has stopped using the pi-top 3 — partly in response to this incident but also because of wider reliability issues with the device. They said some of their grad students will be working on a project with the K-12 team next semester with the aim of creating an alternative that’s more reliable, affordable and safe.
We have also been told of concerns about wider reliability issues with the pi-top 3 by a number of other sources.
We asked pi-top for comment on the safety incident at Cornell Tech and for details of how it responded. The company provided us with a statement in which it claims: “pi–top incorporates all possible safeguards into our products to ensure they are safe.”
“As soon as we became aware of this incident we immediately investigated what had happened,” it went on. “We discovered that the incident was a one-in-a-million occurrence. The user dropped a piece of metal, with a specific size and shape, under the unit. This fell in such a way that it touched a particular pin and caused a linear regulator to heat up. They received a small minor burn to the tip of one finger when they tried to recover that piece of metal.”
“This is the only reported incident where a user has been hurt whilst using one of our products,” pi-top added.
It is not clear how many pi-top 3 laptops have been sold to schools at this stage because pi-top does not break out sales per product. Instead it provided us with a figure for the total number of devices sold since it was founded in 2014 — saying this amounts to “more than 200,000 devices in 4 years which have been used by more than half a million people”.
pi-top also says it has sold products to schools in 70 countries, saying “thousands” of schools have engaged with its products. (The bright green color of the laptop is easy to spot in promotional photos for school STEM programs and summer camps.)
The London-based DIY hardware startup began life around five years ago offering a ‘3D-print it yourself‘ laptop for makers via the Kickstarter crowdfunding platform before shifting its focus to the educational market — tapping into the momentum around STEM education that’s seen a plethora of ‘learn to code’ toys unboxed in recent years.
pi-top has raised more than $20M in VC funding to date and now sells a number of learning devices and plug-in components intended for schools to teach STEM — all of which build on the Raspberry Pi microprocessor.
pi-top adds its own layer of software to the Pi as well as hardware additions intended to expand the learning utility (such as a speaker for the pi-top 3 and an “inventors kit” with several electronics projects, including one that lets kids build and program a robot).
The pi-top 3 — its third device — was launched in October 2017, priced between $285-$320 per laptop (without or with a Raspberry Pi 3).
The distinctively bright green laptop is intended for use by students as young as eight years old.
Unusual failure mode
In the internal email discussing the “Cornell failure diagnosis” — which is dated July 16 — pi-top’s head of support and customer success, Preya Wylie, conveys the assessment of its VP of technology, Wil Bennett, that the “unusual failure mode was likely caused by an electrical short on the male 34-pin connector on the underside of the protoboard”.
She goes on to specify that the short would have been caused by the metal SD-card removal tool that’s bundled with the product — noting this was “reported to have been somewhere underneath the protoboard at the time”.
“[Bennett] has recreated the same conditions on his bench in China and has seen the pi-top enter similar failure modes, with an electrical short and subsequent overheating,” she writes.
An additional complication discussed in the email is that the component is designed to stay on at all times in order that the pi-top can respond to the power button being pressed when the unit is off. Wylie writes that this means, if shorted, the component remains “very hot” even when the pi-top has been shut down and unplugged — as heat is generated by the pi-top continuing to draw power from the battery.
Only once the battery has fully depleted will the component be able to cool down.
In the email — which was sent to pi-top’s founder and CEO Jesse Lozano and COO Paul Callaghan — she goes on to include a list of four “initial recommendations to ensure this does not happen again”, including that the company should inform teachers to remove the SD-card removal tool from all pi-top 3 laptops and to remove the SD card themselves rather than letting students do it; as well as advising teachers/users to turn the device off if they suspect something has got lost under the protoboard.
Another recommendation listed in the email is the possibility of creating a “simple plastic cover to go over the hub” to prevent the risk of users’ fingers coming into contact with hot components.
A final suggestion is a small modification to the board to cut off one of the pins to “greatly reduce the chance of this happening again”.

We asked pi-top to confirm what steps it has taken to mitigate the risk of pi–top 3 components overheating and posing a safety risk via the same sort of shorting failure experienced by Cornell Tech — and to confirm whether it has informed existing users of the risk from this failure mode.
An internal pi-top sales document that we’ve also reviewed discusses a ‘back to school’ sales campaign — detailing a plan to use discounts to “dissolve as much pi-top [3] stock as we can over the next 8 weeks”.
This document says US schools will be targeted from mid August; UK schools/educators from early September; and International Schools Groups from early September. It also includes a strategy to go direct to US Private and Charter Schools — on account of “shorter decision making timelines and less seasonal budgets”.
It’s not clear if the document pre-dates the Cornell incident.
In response to our questions, pi-top told us it is now writing to pi-top 3 customers, suggesting it is acting on some of the initial recommendations set out in Wylie’s July 16 email after we raised concerns.
In a statement the company said: “Whilst it is highly unlikely that this would occur again, we are writing to customers to advise them to take a common-sense approach and switch off the unit if something has got lost inside it. We are also advising customers to remove the SD card tool from the unit. These simple actions will make the remote possibility of a recurrence even less likely.”
In parallel, we have heard additional concerns about the wider reliability of the pi-top 3 product — in addition to the shorting incident experienced by Cornell.
One source, who identified themselves as a former pi-top employee, told us that a number of schools have experienced reliability issues with the device. One of the schools named, East Penn School District in the US, confirmed it had experienced problems with the model — telling us it had to return an entire order of 40 of the pi-top 3 laptops after experiencing “a large volume of issues”.
“We had initially purchased 40 pi-tops for middle level computers classes,” assistant superintendent Laura Witman told us. “I met one of the owners, Jesse, at a STEM conference. Conceptually the devices had promise, but functionally we experienced a large volume of issues. The company tried to remedy the situation and in the end refunded our monies. I would say it was learning experience for both our district and the company, but I appreciate how they handled things in the end.”
Witman did not recall any problems with pi-top 3 components overheating.
A US-based STEM summer camp provider that we also contacted to confirm whether it had experienced issues with the pi-top 3 — a device which features prominently in promotional materials for its program — declined to comment. A spokesman for iD Tech’s program told us he was not allowed to talk about the matter.
A separate source familiar with the pi-top 3 also told us the product has suffered from software reliability issues, including crashes and using a lot of processor power, as well as hardware problems related to its battery losing power quickly and/or not charging. This source, who was speaking on condition of anonymity, said they were not aware of any issues related to overheating.
Asked to respond to wider concerns about the pi-top 3’s reliability, pi-top sent us this statement:
pi–top is a growing and dynamic company developing DIY computing tools which we believe can change the world for the better. In the past four and a half years we have shipped hundreds of thousands of products across our entire product range, and pi–top hardware and software have become trusted assets to teachers and students in classrooms from America to Zimbabwe. pi–top products are hard at work even in challenging environments such as the UN’s Kakuma refugee camp in Northern Kenya.
At the heart of our products is the idea that young makers can get inside our computers, learn how they work and build new and invaluable skills for the future. Part of what makes pi–top special, and why kids who’ve never seen inside a computer before think it’s awesome, is that you have to build it yourself straight out of the box and then design, code and make electronic systems with it. We call this learning.
The nature of DIY computing and electronics means that, very occasionally, things can fail. If they do, pi–top’s modular nature means they can be easily replaced. If customers encounter any issues with any of our products our excellent customer support team are always ready to help.
It is important to say that all electronic systems generate heat and Raspberry Pi is no exception. However, at pi–top we do the very best to mitigate thanks to the cutting-edge design of our hardware. Faults on any of our products fall well below accepted thresholds. Although we are proud of this fact, this doesn’t make us complacent and we continually strive to do things better and provide our customers with world-class products that don’t compromise on safety.
Thousands of schools around the world recognise the fantastic benefits the pi–top [3], pi–top CEED, and pi–top [1] brings as a Raspberry Pi-powered device. Our new flagship products, the pi–top [4] and our learning platform, pi–top Further, take coding education to the next level, as a programmable computing module for makers, creators and innovators everywhere. We are proud of our products and the enormous benefits they bring to schools, students and makers around the world.
Internal restructuring
We also recently broke the news that pi-top had laid off a number of staff after losing out on a large education contract. Our sources told us the company is restructuring to implement a new strategy. pi-top confirmed 12 job cuts at that stage. Our sources suggest more cuts are pending.
Some notable names departing pi-top’s payroll in recent weeks are its director of learning and research, William Rankin — formerly a director of learning at Apple — who writes on LinkedIn that he joined pi-top in March 2018 to “develop a constructionist learning framework to support pi-top’s maker computing platform”. Rankin left the business this month, per his LinkedIn profile.
pi-top’s chief education and product officer, Graham Brown-Martin — who joined the business in September 2017, with a remit to lead “learning, product design, brand development and communication strategy” to support growth of its “global education business, community and ecosystem” — also exited recently, leaving last month per his LinkedIn.
In another change this summer pi-top appointed a new executive chairman of its board: Stanley Buchesky, the founder of a US edtech seed fund who previously served in the Trump administration as an interim CFO for the US department for education under secretary of state, Betsy DeVos.
Buchesky’s fund, which is called The EdTech Fund, said it had made an investment in pi-top last month. The size of the investment has not been publicly disclosed.
Buchesky took over the chairman role from pi-top board member and investor Eric Wilkinson: A partner at its Series A investor, Hambro Perks. Wilkinson remains on the pi-top board but no longer as exec chairman.
The job cuts and restructuring could be intended to prepare pi-top for a trade sale to another STEM device maker, according to one of our sources.
Meanwhile pi-top’s latest device, the pi-top 4, represents something of a physical restructuring of its core edtech computing proposition which looks intended to expand the suggestive utility it offers teachers via multiple modular use-cases — from building drones and wheeled robots to enabling sensor-based IoT projects which could check science learning criteria, all powered by pi-top’s encased Raspberry Pi 4.
Out of the box, the pi-top 4 is a computer in a box, not a standalone laptop. (Though pi-top does plan to sell a range of accessories enabling it be plugged in to power a touchscreen tablet or a laptop, and more.)

pi-top is in the process of bringing the pi-top 4 to market after raising almost $200,000 on Kickstarter from more than 500 backers. Early backers have been told to expect it to ship in November.
While pi-top’s predecessor product is stuck with the compute power of the last-gen Raspberry Pi 3 (the pi-top 3 cannot be upgraded to the Raspberry Pi 4), the pi-top 4 will have the more powerful Pi 4 as its engine.
However the latter has encountered some heat management issues of its own.
The Raspberry Pi Foundation recently put out a firmware update that’s intended to reduce the microprocessor’s operating temperature after users had complained it ran hot.
Asked whether the Foundation has any advice on encasing the Raspberry Pi 4, in light of the heat issue, founder Eben Upton told us: “Putting the Pi in a case will tend to cause it to idle at a higher temperature than if it is left in the open. This means there’s less temperature ‘in reserve’, so the Pi will throttle more quickly during a period of sustained high-intensity operation.”
“In general, the advice is to choose a case which is appropriate to your use case, and to update firmware frequently to benefit from improvements to idle power consumption as they come through,” he added.
TechCrunch’s Steve O’Hear contributed to this report
Read Full Article